Yes conducting an Audit Smart Contract is absolutely critical to safeguarding your blockchain investments. Why? Smart contracts, at their core, are self-executing lines of code that handle high-stakes financial transactions and digital asset management. Any hidden vulnerability within these digital agreements could cost you and your stakeholders millions.
Throughout this blog post of Tokenova, you will discover exactly why a smart contract audit is indispensable, what the process entails, and the best tools for auditing smart contracts. You will also learn essential strategies to mitigate risks, boost trust among investors, and ensure smooth compliance with relevant regulations. By the end, you’ll walk away fully equipped to launch secure and robust blockchain projects no matter the size or scope.
But that’s not all. This article goes beyond the basics. You’ll also find:
- Real-world insights from industry experts and auditors
- Strategies for adopting a multi-layered security approach to your code
- Proven best practices for smart contract security audit and code quality
- Insider tips for continuous testing, monitoring, and future-proofing your dApp
Why Makes Smart Contract Audits Essential?
Smart contracts are the backbone of the decentralized web, powering everything from complex decentralized finance (DeFi) platforms to vibrant NFT marketplaces. These contracts automate critical processes and manage digital assets, making them prime targets for malicious actors.
Given the immense value often governed by these lines of code, a robust smart contract security audit is not just a best practice it’s a necessity for any serious blockchain project. Failing to conduct a thorough audit smart contract process can expose projects to devastating financial losses, erode user trust, and create significant compliance issues.
Security Imperative
Security is the paramount reason to initiate a thorough audit smart contract process. Smart contracts, while revolutionary, are susceptible to vulnerabilities just like any other software. However, the immutable nature of blockchain and the direct financial implications amplify the risks associated with these vulnerabilities. Exploits can range from subtle coding errors to fundamental flaws in the contract’s logic, each potentially providing malicious actors with a gateway to drain funds or disrupt operations.
Consider the infamous DAO hack of 2016. A reentrancy vulnerability, a common coding pitfall, allowed an attacker to siphon approximately $60 million in Ether. This event highlighted the critical importance of thorough smart contract audits to identify and mitigate such vulnerabilities.This single event not only caused significant financial damage but also triggered a hard fork of the Ethereum blockchain, demonstrating the profound impact of un-audited smart contracts.
Reentrancy attacks occur when a contract makes an external call to another contract, and the called contract makes a callback to the original contract before the first call has completed. This can lead to unexpected state changes and fund manipulation.
Beyond reentrancy, integer overflow and underflow vulnerabilities can also be exploited. These occur when arithmetic operations result in values exceeding or falling below the maximum or minimum limits of the data type, leading to unpredictable behavior and potentially malicious transactions. Gas limit issues, stemming from inefficient code or unbounded loops, can cause contracts to fail during execution, disrupting critical functionalities.
The threat landscape is constantly evolving. Emerging threats like front-running, where attackers manipulate transaction order to their advantage, and flash loan exploits, which leverage uncollateralized loans to manipulate market prices or exploit contract logic within a single transaction, have become increasingly sophisticated. In 2024, such attacks contributed significantly to the $2.2 billion lost to crypto hacks, emphasizing the need for advanced security measures and continuous monitoring.Only a rigorous smart contract security audit, employing both automated tools and expert manual review, can effectively identify and mitigate these complex and evolving hazards.
Building Trust and Credibility
In the blockchain space, trust is the most valuable currency. Investors, users, and partners are inherently cautious, especially given the history of hacks and scams in the industry. Demonstrating a commitment to security through a transparent audit smart contract process is crucial for building confidence and fostering trust.
📜Smart Contract Insight: A certified audit report from a reputable firm, confirming the absence of critical and major vulnerabilities, acts as a powerful signal of trustworthiness.
For DeFi and NFT platforms, a publicly available smart contract security audit report can be a significant marketing advantage. It showcases accountability and transparency, setting your project apart in a crowded and competitive market. By openly sharing the audited code and detailing the remediation of any identified issues, you project an image of confidence, sincerity, and a genuine commitment to user safety.
These are powerful emotional triggers that resonate deeply with potential stakeholders, encouraging adoption and investment. In a space where reputation is easily tarnished, a successful audit smart contract serves as a badge of honor, signaling a project’s dedication to best practices and user protection.
Ensuring Regulatory Compliance
The regulatory landscape for blockchain and cryptocurrencies underwent significant changes in 2024. Notably, the European Union’s Markets in Crypto-Assets (MiCA) regulation was fully implemented in December 2024, providing a comprehensive framework for digital asset regulation within the EU.
Similarly, in the United States, the Financial Innovation and Technology for the 21st Century Act (FIT21) was passed by the House in May 2024, aiming to establish clear regulatory guidelines for digital assets. These developments underscore the increasing importance of compliance for blockchain projects operating in these jurisdictions.
📜Smart Contract Insight: A compliant codebase is no longer optional; AML and KYC regulations are becoming more prevalent, and token contracts may need to incorporate mechanisms to adhere to these protocols.
While specific compliance requirements vary across jurisdictions, a comprehensive smart contract security audit plays a vital role in ensuring your code aligns with emerging legal frameworks. Auditors can assess whether your smart contracts incorporate necessary compliance features and identify potential legal risks associated with your code’s functionality.
For a deeper dive, check out our article on Blockchain Regulatory Compliance.
The benefits of compliance are manifold:
Legal Protection: Demonstrates proactive compliance with emerging laws, reducing legal liability and potential penalties.
Global Reach: Makes your project accessible to a broader international user base by meeting diverse regulatory standards.
Investor Assurance: Institutional and retail investors are increasingly seeking legally compliant projects to mitigate regulatory risks and ensure the long-term viability of their investments.
By prioritizing compliance through smart contract audits, projects can navigate the evolving regulatory landscape with confidence and position themselves for sustainable growth.
Cost Efficiency Through Prevention
The cost of neglecting smart contract security audits can be astronomical. When vulnerabilities are discovered after a project goes live, the financial repercussions can be catastrophic, far exceeding the investment in preventative audits. In 2024, funds stolen by hacking cryptocurrency platforms surged 21% from the previous year, totaling $2.2 billion, according to a report from blockchain analysis firm Chainalysis. This significant increase underscores the escalating financial risks and the urgent need for robust security measures.
📜Smart Contract Insight: Investing in an audit smart contract early in the development lifecycle offers significant cost savings in the long run.
The cost efficiencies are evident in several areas:
Preventive Savings: Catching bugs during development can save hundreds of thousands, if not millions, of dollars in potential losses from hacks and exploits.
Reduced Downtime: Post-deployment exploits often force projects to halt operations for emergency fixes and security reviews, leading to lost revenue and damaged reputations. An audited contract minimizes the likelihood of such disruptive downtime.
Lower Maintenance Costs: A thoroughly audited contract typically requires fewer emergency patches and updates post-deployment, reducing ongoing maintenance costs and developer time spent on reactive security measures.
Allocating resources for a comprehensive audit smart contract upfront is a small fraction of the potentially massive costs associated with handling a full-blown security crisis later. It’s a proactive investment that safeguards financial resources, protects reputation, and ensures the long-term viability of the project.
Big Profit. Little to No Tax
The Smart Contract Audit Process
A well-defined and meticulously executed smart contract audit process is essential for uncovering vulnerabilities and providing actionable security insights. A structured approach ensures that all critical aspects of the smart contract are thoroughly examined, leaving no stone unturned in the quest for robust security. Professional auditors typically follow a multi-stage process, each step building upon the previous one to deliver a comprehensive security assessment.
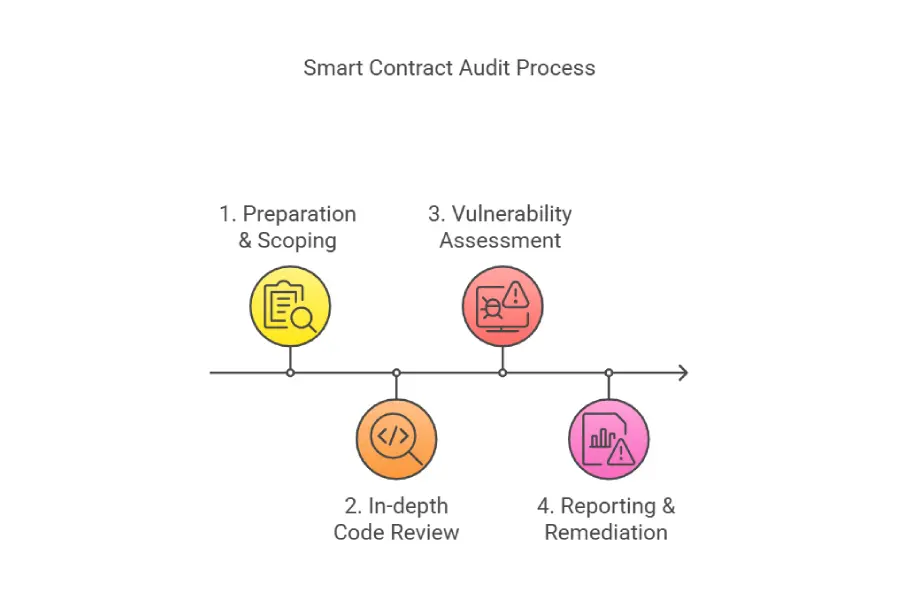
Preparation and Scoping
The preparation phase is crucial for setting the stage for a successful audit smart contract engagement. This initial stage involves gathering all necessary documentation and information to provide auditors with a complete understanding of the project and the smart contracts to be audited. Effective preparation ensures that the audit is focused, efficient, and delivers maximum value.
Key activities in the preparation phase include:
Document Collection: Providing auditors with comprehensive documentation is paramount. This includes technical specifications, architecture diagrams, data flow specifications, and user stories. Clear documentation helps auditors understand the intended functionality, business logic, and context of the smart contract.
Code Readiness: Ensuring the codebase is stable and as close to final as possible is essential. Finalizing functionalities before the smart contract security audit prevents rework, reduces confusion, and ensures that the audit is performed on the code that will be deployed.
Clear Scope Definition: Clearly defining the scope of the audit is critical. This involves specifying which smart contracts are to be audited, the functionalities they encompass, and any specific areas of concern the development team may have. A well-defined scope ensures that the audit focuses on the most critical components and addresses the project’s specific security needs.
Internal Review (Optional but Recommended): Conducting an internal security review before engaging external auditors is a best practice. An internal review serves as a preliminary self-check, allowing the development team to identify and fix any glaring issues before the formal external audit begins. This can streamline the external audit process and reduce costs.
In-depth Code Review
The code review stage is the core of the smart contract audit process. This is where auditors delve into the smart contract code to identify potential vulnerabilities and security weaknesses. Auditors employ a combination of automated scanning tools and meticulous manual examination to achieve comprehensive coverage and accuracy. This dual approach leverages the strengths of both automated and human analysis.
The code review typically involves:
Static Analysis: Automated static analysis tools are employed to parse the codebase and flag suspicious code constructs, potential vulnerabilities like integer overflows, gas inefficiencies, and deviations from coding best practices. Tools like Slither and Securify excel in static analysis, quickly identifying common security pitfalls. Static analysis examines the code without executing it, focusing on code structure and patterns to detect potential issues.
Dynamic Analysis: Dynamic analysis involves evaluating the smart contract’s behavior in a simulated runtime environment. This approach helps catch runtime-specific vulnerabilities, such as reentrancy, front-running potential, and transaction-order dependencies. Tools like Mythril utilize symbolic execution, a form of dynamic analysis, to explore different execution paths and identify potential vulnerabilities that may only manifest during runtime. Dynamic analysis complements static analysis by examining the contract’s behavior under various conditions.
Manual Code Review: Expert auditors manually review the code line by line, examining the contract’s logic, business rules, and potential edge cases. Manual review is crucial for identifying complex vulnerabilities and logic flaws that automated tools may miss. Auditors leverage their deep understanding of smart contract security principles and common attack vectors to uncover subtle weaknesses and ensure the contract’s intended behavior is correctly implemented.
📜Smart Contract Insight: By combining static analysis, dynamic analysis, and manual code review, auditors achieve a comprehensive and rigorous smart contract security audit.
Vulnerability Assessment and Classification
Following the code review, auditors compile a detailed list of all identified vulnerabilities. Each vulnerability is then carefully assessed and classified based on its severity and potential impact. This vulnerability assessment and classification process is crucial for prioritizing remediation efforts and communicating risks effectively to stakeholders.
Vulnerabilities are typically ranked according to severity levels, such as:
Critical: Critical vulnerabilities are the most severe, representing immediate and significant risks. They have the potential to cause substantial financial loss, system compromise, or complete failure of the smart contract. Examples include vulnerabilities that allow attackers to drain funds, take control of the contract, or halt critical operations.
High: High-severity vulnerabilities pose significant risks and could lead to substantial financial loss or operational disruption. They are less severe than critical vulnerabilities but still require immediate attention and remediation.
Medium: Medium severity vulnerabilities represent moderate risks and could potentially be exploited to cause limited financial loss or operational impact. These vulnerabilities should be addressed in a timely manner.
Low: Low-severity vulnerabilities are minor issues that may slightly degrade performance, cause minor malfunctions, or represent potential best practice violations. While less critical, these issues should still be addressed to improve overall code quality and security posture.
Informational: Informational findings are not vulnerabilities but rather suggestions for code improvements, gas optimizations, or adherence to best practices. These findings enhance code quality and maintainability but do not represent immediate security risks.
Common vulnerability checks during this stage include:
Reentrancy Testing: Specifically testing for reentrancy vulnerabilities by simulating external calls and callbacks to disrupt the expected contract flow.
Front-Running Analysis: Verifying that no function or contract state is exposed to potential manipulation between transaction broadcast and validation, mitigating front-running risks.
Logic Error Verification: Ensuring the smart contract accurately enforces the intended business logic, particularly in critical areas such as token distribution, governance rules, and access control mechanisms.
Gas Limit and Optimization Checks: Analyzing code for gas inefficiencies and potential gas limit issues that could lead to denial-of-service or unexpected contract behavior.
Access Control Review: Verifying that access control mechanisms are correctly implemented and prevent unauthorized access to sensitive functions or data.
Reporting and Remediation
The culmination of the smart contract audit process is the delivery of a comprehensive audit report. This report serves as the primary communication tool, conveying the audit findings, vulnerability assessments, and recommended remediation steps to the project team and stakeholders. A well-structured and detailed report is essential for effective communication and action.
A comprehensive smart contract security audit report typically includes:
Executive Summary
Provides stakeholders with a high-level overview of the audit process, key findings, and overall security posture of the smart contract. The executive summary is intended for non-technical audiences and provides a concise summary of the audit’s outcome.
Technical Analysis
Details each identified vulnerability with specific code references, descriptions of the vulnerability, severity ratings, and potential exploit scenarios. The technical analysis section provides in-depth information for developers to understand and address each vulnerability.
Remediation Steps
Offers clear and actionable recommendations for fixing each identified vulnerability and improving the overall security of the smart contract. Remediation steps often include code examples, best practice guidelines, and specific changes to implement.
Final Outcome and Re-Audit (Optional but Recommended)
Indicates the overall security status of the contract post-remediation. Ideally, the audit process includes a re-check or re-audit phase, where auditors verify that the developer-implemented fixes have successfully mitigated the identified risks. A re-audit provides assurance that the vulnerabilities have been effectively addressed and the contract is secure.
By meticulously following each step of the audit smart contract process, projects can significantly reduce the risk of catastrophic exploits, build trust with users and investors, and foster an environment of transparency and security. The audit report serves as a valuable deliverable, providing actionable insights and guidance for enhancing smart contract security.
Top Tools for Auditing Smart Contracts
The landscape of smart contract audit tools is constantly evolving, with new tools and updates emerging regularly to address the ever-changing threat environment. While no single tool can guarantee bulletproof security, leveraging a combination of the best tools for auditing smart contracts is a crucial component of a holistic security strategy. These tools automate various aspects of the audit process, enhancing efficiency and coverage.
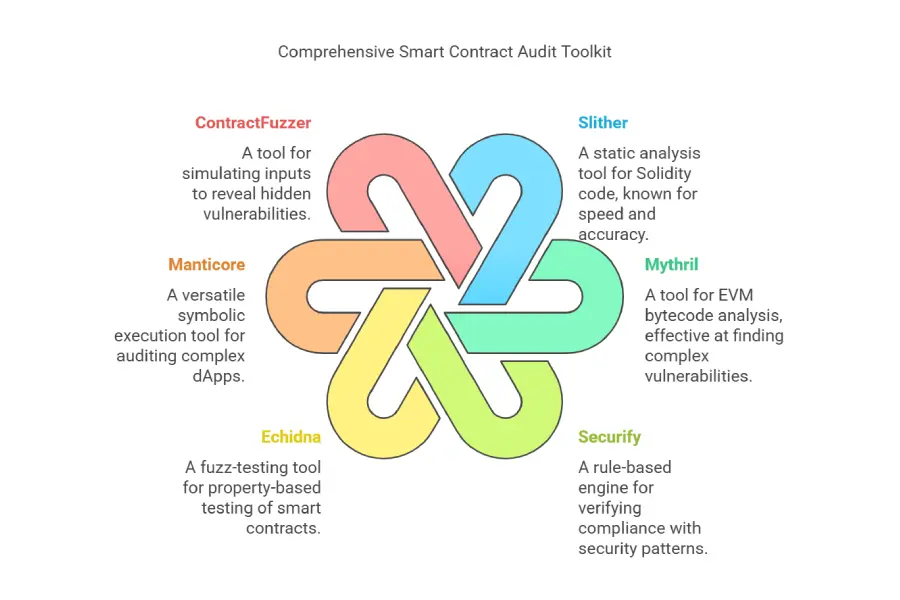
Slither: Static Analysis Powerhouse
Slither, developed by Trail of Bits, is a leading static analysis framework specifically designed for Solidity code. It stands out for its speed, accuracy, and comprehensive set of detectors that scan for a wide range of vulnerabilities. Slither excels at identifying common security pitfalls, gas optimization opportunities, and code quality issues. Its ease of use and robust features make it a staple for both independent developers and professional smart contract security audit firms.
Key Features:
Rapid Vulnerability Detection: Slither quickly identifies common security vulnerabilities such as reentrancy, integer overflows/underflows, unchecked send/transfer, and more. Its detectors are continuously updated to address new and emerging threats.
Thorough Code Instrumentation: Slither provides detailed code instrumentation, offering insights into control flow, data dependencies, and potential attack vectors. This helps auditors understand the code’s behavior and identify subtle vulnerabilities.
Gas Optimization Suggestions: Slither goes beyond security and provides helpful suggestions for optimizing gas usage. Efficient gas usage is crucial for cost-effective smart contract deployments, and Slither helps developers identify areas for improvement.
Customizable Detectors: Slither allows users to create custom detectors to identify project-specific vulnerabilities or enforce coding standards. This extensibility makes Slither adaptable to various project needs.
Mythril: Symbolic Execution for Deep Bug Hunting
Mythril is a powerful symbolic execution tool that focuses on EVM bytecode analysis. This bytecode-level analysis makes Mythril highly effective at uncovering complex vulnerabilities that may be missed by source code analyzers. Mythril excels at finding reentrancy vulnerabilities, transaction-ordering dependencies, and other logic flaws that can be challenging to detect through static analysis alone. By virtually executing the code under numerous constraints, Mythril explores different execution paths and identifies potential vulnerabilities that may only manifest under specific conditions.
Key Features:
Symbolic Execution Engine: Mythril’s symbolic execution engine allows for deeper detection of hidden bugs by exploring all possible execution paths and states of the smart contract. This comprehensive analysis helps uncover vulnerabilities that may not be apparent through static analysis.
Transaction-Order Dependency Detection: Mythril is particularly effective at detecting transaction-order dependency issues, where the outcome of a transaction depends on the order in which transactions are processed. These vulnerabilities can be exploited to manipulate contract state or gain unauthorized access.
Configurable Scanning Levels: Mythril offers configurable scanning levels, allowing users to adjust the depth and intensity of the analysis based on their specific audit needs and time constraints. This flexibility makes Mythril suitable for both quick scans and in-depth security assessments.
Integration with Development Workflows: Mythril can be integrated into development workflows and CI/CD pipelines, enabling continuous security testing and early vulnerability detection.
Securify: Rule-Based Security Pattern Verification
Securify, developed by ETH Zurich, is an automated analysis tool that takes a unique approach to smart contract security audit. Instead of focusing on specific vulnerability types, Securify checks for compliance with predefined security patterns. It uses a rule-based engine to verify whether the smart contract adheres to established security best practices and patterns. Securify provides a pass/fail verdict for each pattern it tests, offering a clear and concise assessment of security compliance.
Key Features:
Rule-Based Engine: Securify’s rule-based engine checks for compliance with a comprehensive set of security patterns, covering various aspects of smart contract security. This pattern-based approach provides a structured and systematic way to assess security.
Clear Vulnerability Documentation: Securify provides clear and detailed documentation for each vulnerability it discovers, explaining the nature of the vulnerability, its potential impact, and recommended remediation steps. This documentation helps developers understand and address the identified issues effectively.
User-Friendly Dashboard: Securify offers a user-friendly dashboard that provides a quick and intuitive interpretation of audit results. The dashboard visualizes security compliance and highlights areas that require attention.
Formal Verification Techniques: Securify leverages formal verification techniques to mathematically prove or disprove the presence of certain security properties in the smart contract. This rigorous approach enhances the reliability and accuracy of the security assessment.
Additional Power Tools for Comprehensive Audits
Beyond Slither, Mythril, and Securify, several other powerful tools can enhance your smart contract audit toolkit:
Echidna: Echidna is a robust fuzz-testing tool specifically designed for smart contracts. Fuzzing involves feeding random or crafted inputs to the contract to uncover unexpected behavior and vulnerabilities. Echidna excels at property-based testing, allowing auditors to define security properties and automatically generate test cases to verify these properties.
Manticore: Manticore is another symbolic execution tool that offers versatility by handling both binaries and EVM bytecode. This makes it suitable for auditing complex dApps that may involve multiple components and languages. Manticore provides advanced symbolic execution capabilities for in-depth vulnerability analysis.
ContractFuzzer: ContractFuzzer is a specialized fuzzing tool focused on revealing hidden vulnerabilities in smart contracts. It simulates random and crafted inputs to trigger unexpected behavior and identify potential attack vectors. ContractFuzzer is particularly effective at finding edge cases and unexpected interactions.
These best tools for auditing smart contracts should ideally be used in combination with manual code reviews by experienced auditors. While automation provides efficiency and broad coverage, human expertise remains indispensable for identifying complex logic flaws, understanding the business context, and providing nuanced security recommendations. A balanced approach combining automated tools and manual review delivers the most comprehensive and effective smart contract security audit.
Best Practices for Smart Contract Audits
Conducting a smart contract security audit effectively requires adherence to recognized best practices. These practices ensure that the audit is thorough, and efficient, and delivers actionable results. Following these guidelines significantly enhances the quality and outcomes of the audit process, maximizing the security benefits for your blockchain project.
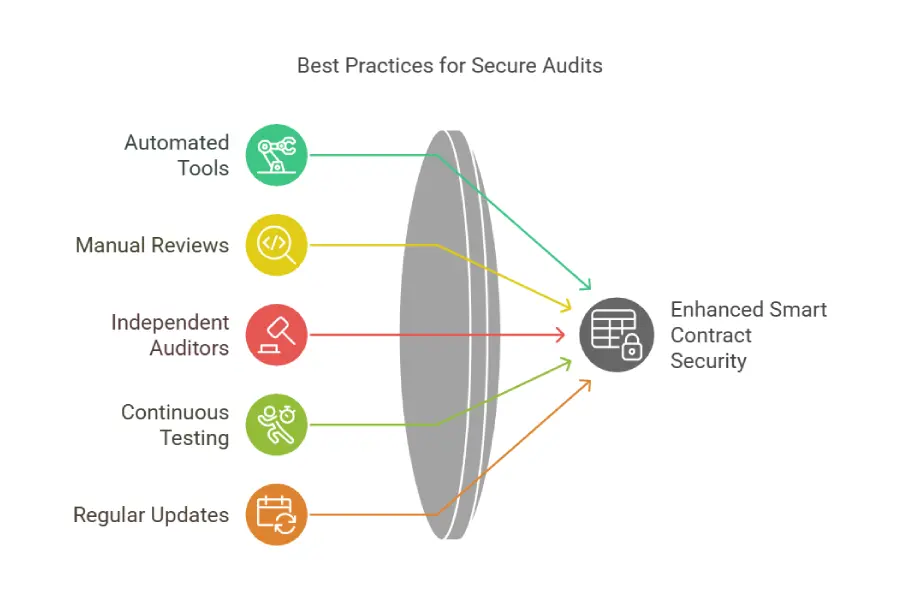
Combining Automated Tools and Manual Code Reviews
While automated tools are invaluable for quickly identifying common vulnerabilities and improving audit efficiency, they are not a silver bullet. Automated scans can generate false positives, miss nuanced logic errors, and lack the contextual understanding that human auditors possess. Therefore, a best practice in smart contract security audit is to combine automated tools with thorough manual code reviews.
The synergy between automated and manual approaches is crucial:
Automated Analysis for Efficiency: Automated tools excel at quickly scanning large codebases, identifying low-hanging fruit vulnerabilities, and enforcing coding standards. They provide broad coverage and improve audit efficiency by automating repetitive tasks.
Manual Review for Depth and Context: Skilled auditors bring human expertise, intuition, and contextual understanding to the audit process. They manually step through the code, analyze complex logic flows, examine edge cases, and confirm or debunk findings from automated tools. Manual review is essential for uncovering sophisticated vulnerabilities and logic flaws that automated tools may miss.
By combining the speed and breadth of automated analysis with the depth and context of manual review, projects can achieve a more comprehensive and effective audit smart contract process. This balanced approach maximizes vulnerability detection and ensures a higher level of security assurance.
Integrating Continuous Testing and Monitoring
Security in the blockchain space is not a one-time event; it’s an ongoing process and new vulnerabilities may emerge over time. Therefore, integrating continuous testing and monitoring into the smart contract lifecycle is a critical best practice. This proactive approach helps developers identify anomalies early, detect regressions, and maintain a strong security posture over time.
Key components of continuous testing and monitoring include:
Automated Unit Testing: Implementing automated unit tests to confirm the functionality of individual smart contract components is essential. Unit tests verify that each function behaves as expected under various conditions, helping to catch bugs early in the development process.
Integration Testing: Evaluating how multiple smart contracts interact with each other through integration testing is crucial for complex dApps. Integration tests ensure that contracts work seamlessly together and prevent vulnerabilities arising from inter-contract interactions.
Live Monitoring and Alerting: Implementing real-time monitoring tools like Tenderly or Dune Analytics allows for continuous tracking of contract transactions, gas usage, and other key metrics. Setting up alerts for suspicious activity or anomalies enables early detection of potential exploits or attacks in a live environment.
📜Smart Contract Insight: By integrating continuous testing and monitoring, projects can shift from a reactive security approach to a proactive one, ensuring ongoing security and resilience for their smart contracts.
Engaging Independent Third-Party Auditors
Engaging independent third-party auditors for smart contract security audit is a crucial best practice for obtaining an unbiased and objective security assessment. External auditors bring a fresh perspective, unencumbered by the biases or assumptions of internal development teams. Their specialized expertise and systematic review processes enhance the rigor and credibility of the audit.
The benefits of engaging third-party auditors are significant:
Unbiased Perspective: External auditors provide an objective and unbiased assessment of the smart contract’s security, free from internal biases or assumptions. This fresh perspective can uncover vulnerabilities that internal teams may overlook.
Specialized Expertise: Professional smart contract security audit firms specialize in blockchain security and possess deep expertise in identifying and mitigating smart contract vulnerabilities. They stay up-to-date with the latest attack vectors and security best practices.
Systematic Review Processes: Reputable audit firms follow systematic and well-defined review processes honed by experience. These processes ensure thorough coverage and consistent quality in the audit.
Credibility and Trust Boost: A seal of approval from a respected third-party audit firm significantly enhances the project’s credibility and builds trust with investors, users, and partners. A publicly available audit report demonstrates a commitment to security and transparency.
📜Smart Contract Insight: Choosing a reputable and experienced third-party audit firm is a critical investment in smart contract security and project success.
Regularly Updating Audits for Evolving Threats
The blockchain landscape is dynamic, with new vulnerabilities, attack techniques, and regulatory requirements emerging constantly. Therefore, a one-time smart contract security audit is not sufficient for long-term security. Regularly updating audits is a crucial best practice to ensure ongoing resilience and adapt to the evolving threat environment.
Reasons for regularly updating audits include:
Feature Upgrades and Code Changes: Adding new functionalities, updating existing code, or refactoring contracts can inadvertently introduce new vulnerabilities. Any significant code change should be followed by a re-audit to ensure security is maintained.
Shifting Regulatory Landscape: Evolving compliance standards and regulatory requirements may necessitate code tweaks or updates to maintain legal compliance. Regular audits help ensure ongoing compliance with the latest regulations.
Emerging Threats and Attack Vectors: Attack techniques and vulnerability discovery methods are constantly evolving. Regular audits help identify and mitigate newly discovered threats and ensure the smart contract remains resilient against the latest attack vectors.
Implementing a schedule for periodic mini-audits or establishing ongoing bug bounty programs are effective strategies for ensuring your smart contract remains secure in an ever-changing environment. Proactive and continuous security efforts are essential for long-term project success and user protection.
“Insider Insights”: Elevate Your Contract Security
To truly excel in smart contract security and stand out in the competitive blockchain market, it’s essential to go beyond the basics and adopt advanced strategies. These “insider insights” address often-overlooked areas that can dramatically strengthen your defenses and enhance overall performance.
Building Security in from Day One: Secure by Design
Many projects treat security as an afterthought, scheduling an audit smart contract only near the end of development or even post-launch. This reactive approach is shortsighted and inefficient. A more effective strategy is to adopt “Secure by Design” principles from the very beginning of the development lifecycle. This proactive approach integrates security considerations into every stage of development, from design to deployment.
Implementing “Secure by Design” involves:
Security Requirements Engineering: Defining security requirements upfront and incorporating them into the project’s specifications.
Secure Coding Practices: Encouraging developers to follow secure coding standards, such as the Solidity style guide, and incorporating security checks into code commits.
Threat Modeling: Proactively identifying potential threats and attack vectors during the design phase and designing mitigations into the contract architecture.
Security Training for Developers: Providing developers with security training to enhance their awareness of common vulnerabilities and secure coding techniques.
Using Security Libraries and Frameworks: Leveraging well-vetted security libraries and frameworks to reduce the risk of introducing common vulnerabilities.
📜Smart Contract Insight: By building security from day one, projects can significantly reduce the likelihood of vulnerabilities and create more robust and secure smart contracts.
Cultivating a “Security-First” Culture
Organizational culture plays a vital role in smart contract security. Cultivating a “security-first” culture within your development team and organization as a whole is a powerful defense mechanism. This culture emphasizes security awareness, proactive risk identification, and continuous improvement.
Fostering a “security-first” culture involves:
Promoting Security Awareness: Regularly communicating the importance of security to all team members and providing ongoing security awareness training.
Encouraging Timely Code Reviews: Making code reviews a mandatory part of the development process and emphasizing security considerations during reviews.
Open Discussion of Security Risks: Creating a safe and open environment where team members feel comfortable discussing potential security risks and vulnerabilities without fear of blame.
Proactive Threat Modeling Sessions: Conducting regular threat modeling sessions to identify and analyze potential threats and vulnerabilities.
Internal Bug Bounty Programs: Offering incentives, such as internal bug bounties, for developers and team members who identify and report vulnerabilities. This transforms the entire team into an extended security force.
📜Smart Contract Insight: A strong “security-first” culture empowers the entire organization to contribute to security and creates a more resilient and secure development environment.
Your Vision, Realized!
Thorough Documentation for Compliance and Clarity
Comprehensive documentation is not just for user manuals; it’s also crucial for smart contract security and compliance. Thorough documentation helps auditors understand the rationale behind coding choices, business logic, and intended functionality. This clarity leads to more accurate audit findings and targeted recommendations.
Effective documentation includes:
Architecture Diagrams: Visual representations of the smart contract architecture, showing contract interactions and data flows.
Technical Specifications: Detailed descriptions of contract functionalities, business logic, and intended behavior.
Code Comments: Clear and concise comments within the code explaining complex logic, function purpose, and security considerations.
Security Considerations Documentation: Explicitly documenting security design choices, implemented security mechanisms, and potential security risks.
Well-structured documentation also proves invaluable during compliance checks, where regulators require clarity on how a contract functions and how controls are enforced. Thorough documentation enhances transparency, facilitates audits, and supports compliance efforts.
Implementing Layered Security Mechanisms: Defense in Depth
Relying on a single security measure is risky. A best practice in smart contract security is to implement layered security mechanisms, also known as “defense in depth.” This approach involves deploying multiple lines of defense to protect against various attack vectors. If one security layer fails, others remain to thwart potential exploits.
Examples of layered security mechanisms include:
Multi-Signature Wallets: Requiring multiple key approvals for critical actions, such as contract upgrades or fund withdrawals, to prevent single points of failure.
Circuit Breakers: Implementing mechanisms to halt specific operations or the entire contract if abnormal activity or predefined thresholds are detected. Circuit breakers provide a safety net in case of unexpected events or attacks.
Rate Limiters: Restricting how often particular functions can be called to prevent denial-of-service attacks or abuse of gas-intensive functions.
Access Control Lists (ACLs): Implementing fine-grained access control lists to restrict access to sensitive functions and data to authorized users or contracts.
Input Validation: Rigorous input validation to prevent injection attacks and ensure data integrity.
A layered security approach provides a more robust and resilient defense against a wide range of threats, significantly enhancing smart contract security.
Embracing Open-Source Audits and Community Scrutiny
Consider open-sourcing your smart contract code to leverage the collective intelligence of the open-source community. Open-source scrutiny can complement professional audits by providing an additional layer of security review. The open-source community often uncovers hidden flaws or suggests performance improvements in a more agile manner than a single auditor could.
Benefits of embracing open-source audits include:
Crowdsourced Security Review: The open-source community provides a large pool of security-minded developers and researchers who can review the code and identify potential vulnerabilities.
Faster Vulnerability Discovery: Open-source scrutiny can lead to faster vulnerability discovery and reporting compared to relying solely on internal or closed-source audits.
Community-Driven Improvements: The open-source community can contribute code improvements, bug fixes, and security patches, enhancing the overall quality and security of the smart contract.
Increased Transparency and Trust: Open-sourcing code promotes transparency and builds trust with users and the community, demonstrating a commitment to openness and collaboration.
By coupling open-source scrutiny with professional smart contract security audits, projects can maximize their coverage against potential threats and benefit from the collective wisdom of the blockchain community.
Tokenova Services
Looking for a partner to bolster your smart contract security? Tokenova offers end-to-end Audit Smart Contract services, tailored to your project’s unique needs. With a seasoned team of blockchain experts, we leverage both advanced smart contract audit tools and thorough manual inspections to spot even the most elusive vulnerabilities. Our proven track record spans DeFi platforms, NFT marketplaces, and enterprise-grade blockchains.
Why Choose Tokenova?
- Comprehensive Assessment: We go beyond simple code reviews, examining everything from tokenomic models to operational workflows.
Custom Reporting: Receive clear, actionable reports with best-practice recommendations.
24/7 Post-Audit Support: Stay secure post-deployment with continuous monitoring, monthly check-ins, and emergency patch deployment services.
Global Network: Our relationships with major auditors and regulators help streamline compliance efforts and future funding rounds.
Conclusion
By now, it should be crystal clear that an Audit Smart Contract process is one of the most critical pillars supporting the blockchain landscape. From mitigating the risk of catastrophic hacks to establishing trust and meeting compliance requirements, thorough audits form the bedrock of sustainable, high-performing decentralized applications. In the rapidly evolving world of blockchain, where innovation and security must go hand-in-hand, prioritizing smart contract security audit is not just a recommendation it’s a fundamental requirement for success.
In a volatile industry where billions of dollars can shift hands in the blink of an eye, ignoring a smart contract security audit is an invitation to potential disaster. However, by embracing a combination of forward-thinking development practices, leveraging robust smart contract audit tools, conducting meticulous manual code reviews, and ensuring transparent reporting, projects can dramatically reduce these risks. Whether you’re a startup founder, an established enterprise, or an investor looking to deploy new blockchain solutions, prioritizing security through audit smart contract processes pays off handsomely in reputation, cost savings, and long-term success.
Remember: every detail matters. From ensuring your code is neatly documented and thoroughly tested to adopting layered security strategies and staying informed about emerging threats each small step contributes to a more resilient project. The future of blockchain belongs to those who can innovate securely, responsibly, and transparently. Let your venture be among them, fortified by the assurance of a rigorous smart contract audit.
Key Takeaways
Security is Paramount: Vulnerabilities like reentrancy, integer overflows, and gas issues can be financially devastating.
Trust is Non-Negotiable: A verified Audit Smart Contract process can be your strongest marketing tool, building credibility among investors and stakeholders.
Compliance Meets Opportunity: Aligning with regulations and best practices expands your reach and protects you legally.
Use the Best Tools: Don’t rely solely on automated scans; combine tools like Slither, Mythril, Securify with manual reviews for comprehensive protection.
Evolving Landscape: Ongoing audits, real-time monitoring, and layered security measures are essential in the fast-paced blockchain environment.
How does an audit differ from a regular security assessment for blockchain projects?
An audit smart contract focuses on diving deep into the contract’s code structure, functional logic, and potential vulnerabilities unique to smart contract environments. A general security assessment might only offer high-level checks without the specialized knowledge of blockchain mechanisms, such as gas optimizations, reentrancy vulnerabilities, or transaction-order dependencies. A smart contract security audit requires specialized expertise in blockchain technology, smart contract languages like Solidity, and common attack vectors specific to decentralized applications.
How does an audit differ from a regular security assessment for blockchain projects?
An audit smart contract focuses on diving deep into the contract’s code structure, functional logic, and potential vulnerabilities unique to smart contract environments. A general security assessment might only offer high-level checks without the specialized knowledge of blockchain mechanisms, such as gas optimizations, reentrancy vulnerabilities, or transaction-order dependencies. A smart contract security audit requires specialized expertise in blockchain technology, smart contract languages like Solidity, and common attack vectors specific to decentralized applications.
Do smaller blockchain initiatives also need to invest in smart contract audits?
Absolutely. Smaller projects can become easy targets precisely because they may skimp on security. Whether you’re handling $1,000 or $1 million in assets, a successful exploit can wipe out your funds, damage your reputation, and derail your roadmap. An audit smart contract process protects your users and your brand image, regardless of scale. For smaller initiatives, the cost of an audit smart contract is a worthwhile investment to prevent potentially devastating financial and reputational losses.
What if I have multiple contracts that need auditing simultaneously?
You can audit smart contract multiple contracts concurrently as long as you plan the process effectively. Professional audit firms often run parallel analyses, focusing on each contract’s unique functionality, while also examining interactions between contracts. This holistic approach ensures no exploitable gaps emerge from cross-functional dependencies. Auditing multiple contracts simultaneously requires careful coordination and a structured approach to ensure comprehensive coverage and efficient resource allocation.