Data is one of the most valuable assets in the digital world, and protecting it has never been more critical. With cyber threats increasing in sophistication and frequency, organizations are constantly looking for the best ways to secure sensitive information from unauthorized access, data breaches, and compliance violations. This is where tokenization, encryption, and hashing come into play three essential security techniques that help protect data in different ways.
However, many businesses struggle to determine which method is best suited for their specific security needs. Should they encrypt sensitive data, tokenize it, or apply hashing? Is tokenization the same as encryption, and what makes tokenization vs hashing fundamentally different? These questions are crucial because choosing the right approach affects everything from compliance with regulations like PCI DSS and GDPR to system performance, security risk management, and operational efficiency.
This guide provides a clear, in-depth exploration of tokenization vs encryption vs hashing, detailing how each method works, where they should be applied, and how they compare. We will break down the key differences, discuss practical use cases, and help you understand the encryption and tokenization differences so you can make informed decisions about securing your data.
Data Security Essentials: Tokenization, Encryption, and Hashing
In cybersecurity, tokenization, encryption, and hashing are key players in safeguarding sensitive information. Each uses different methods to protect data, and understanding their unique roles is vital for any strong security plan. They all contribute to keeping data safe and trustworthy but in distinct ways.
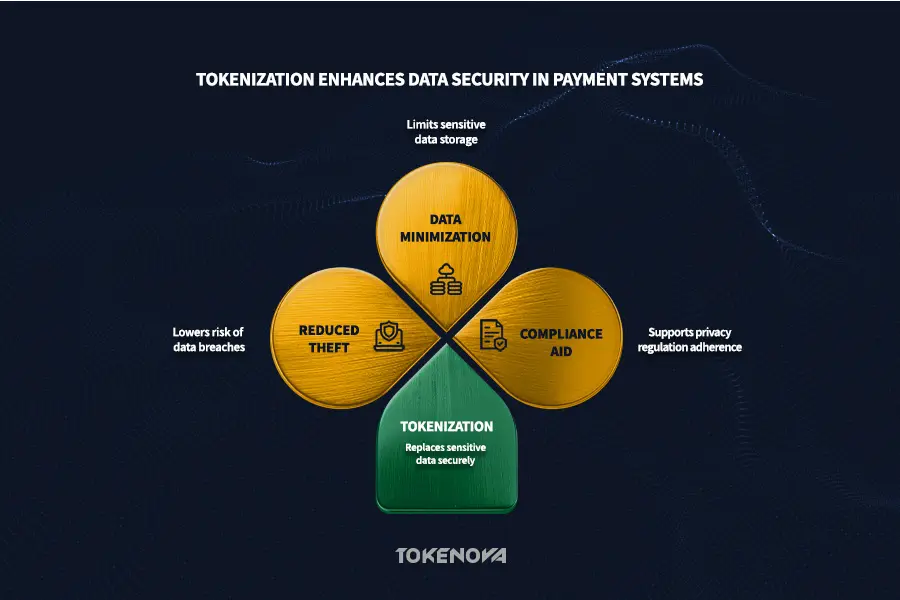
Tokenization is like swapping out real valuables for fakes. It replaces sensitive data with non-sensitive substitutes called tokens. Think of using a token instead of your actual credit card number for online purchases. The token is useless to hackers because it can’t be reversed to get back to your real card details. This is super useful for payment processing, keeping your real information out of reach.
Encryption is about scrambling data to make it unreadable, like locking up your files in a digital safe. It turns your normal text into ciphertext, which looks like gibberish. Only someone with the right “key” can unlock it and turn it back into readable text. Encryption is crucial for keeping communications private and protecting stored data, ensuring that even if someone steals data, they can’t understand it without the key.
Hashing is like creating a unique digital fingerprint for data. It uses a one-way process to make a fixed-size code, the hash, from any piece of data. This hash is unique and can’t be reversed to find the original data. Hashing is mainly used to check if data is unchanged and to securely store passwords. When you log in, the system hashes your password and checks if it matches the stored hash, verifying you without ever storing your actual password plainly.
These three methods are the backbone of data security. Knowing how they differ and when to use each one is key to building a solid defense against data breaches and cyber threats.
Tokenization: Data Substitution in Detail
Tokenization is essentially the process of replacing sensitive data with non-sensitive stand-ins, or tokens. Technically, it relies on a tokenization engine or vault. When sensitive information enters a system, this engine kicks in, creating a random, non-sensitive token to take its place. This token is then used everywhere the real data would have been, while the actual sensitive data is locked away securely in a token vault.
Imagine using a voucher instead of real money in a game arcade. The voucher (token) lets you play games, but it’s not real cash and can only be used within the arcade system. Similarly, data tokens represent sensitive information without exposing the real deal.
Where Tokenization Shines:
Tokenization significantly enhances payment processing security, especially for credit cards. Instead of storing actual card numbers, businesses use tokens, reducing the risk of theft. When you pay online, your card details are converted into a token for processing, leaving hackers with only useless tokens in case of a breach. Tokenization also aids data minimization, helping businesses limit sensitive data storage and comply with privacy regulations like GDPR and CCPA. For example, hospitals can tokenize patient IDs, allowing researchers access to necessary data without revealing identities. Additionally, storing tokens instead of sensitive data in databases adds a layer of defense against attacks, as breached tokens alone are worthless without the secure token vault.
Encryption: The Cipher of Confidentiality
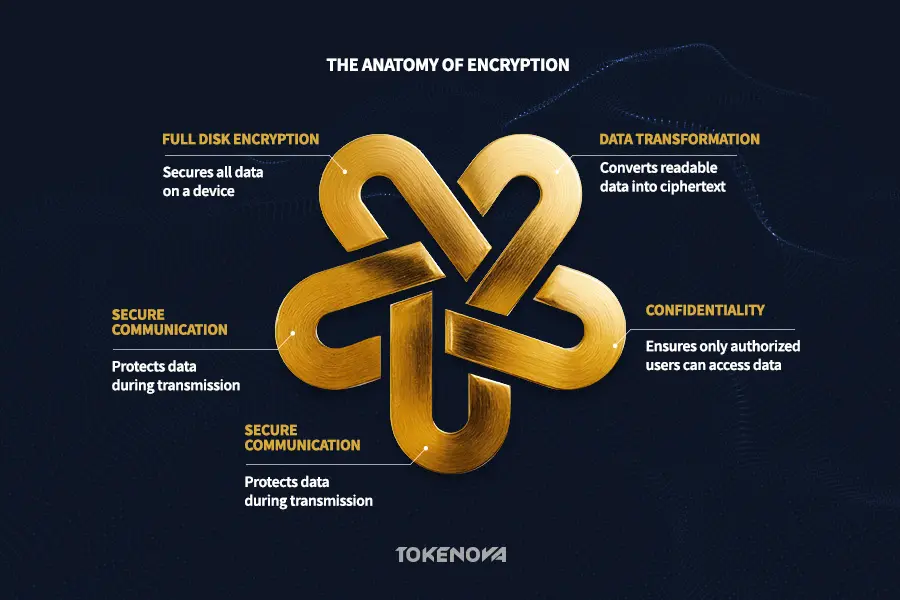
Encryption is a method that transforms your data into ciphertext, an unreadable format, ensuring confidentiality. Technically speaking, encryption algorithms use complex math and keys to jumble up data. The process takes readable plaintext and turns it into ciphertext using an algorithm and a key. To get back to the original plaintext, you need the right decryption key and algorithm.
Think of encryption as whispering secrets in code. Without knowing the code (the decryption key), the secret message is just noise. Encryption works the same way digitally, keeping your data private even if intercepted.
Encryption’s Key Uses:
Encryption is vital for protecting data confidentiality, whether in transit or at rest. It safeguards sensitive information, such as personal details and financial records, from unauthorized access. For instance, encrypted emails ensure only you and the recipient can read the messages. Encryption underpins secure online communication, with technologies like HTTPS securing data between your browser and websites.
VPNs also employ encryption to protect internet traffic from prying eyes, especially on public Wi-Fi. Additionally, encrypting data stored on devices, in databases, or in the cloud defends against data theft. Even if devices are compromised, encrypted data remains secure, as thieves lack the keys to access it. Full disk encryption protects everything on your hard drive, providing comprehensive security.
Hashing: The Integrity Guardian
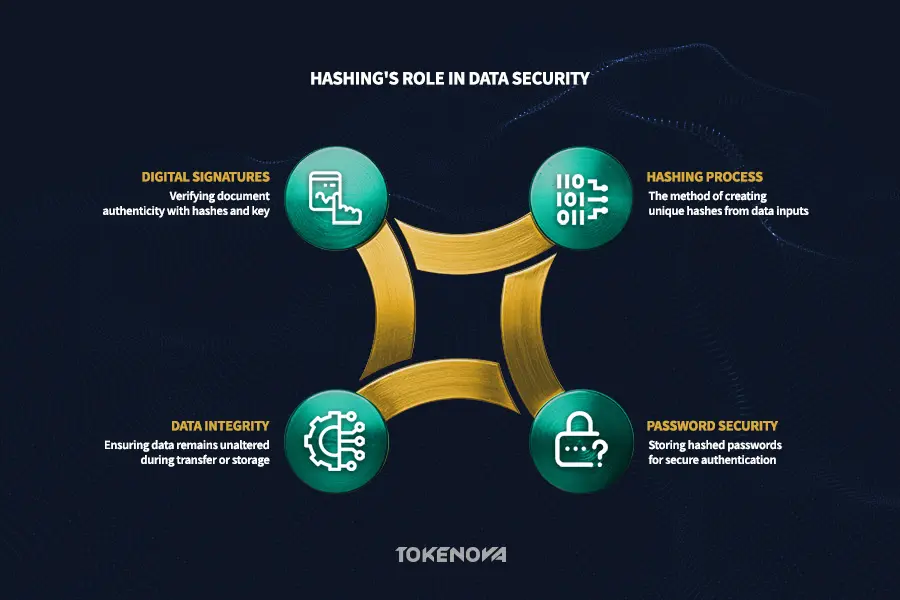
Hashing is a cryptographic process that creates a unique, fixed-size string, or hash, from any data input. Technically, hashing algorithms are designed to be one-way functions. This means you can easily create a hash from data, but it’s practically impossible to reverse the process and get the original data back from the hash. Even a tiny change in the original data will produce a completely different hash, making hashing very sensitive to changes.
Imagine hashing as creating a digital seal for a document. This seal is unique to the document and proves it’s original and unaltered. If anyone tries to tamper with the document, the seal will break (the hash value will change), immediately showing that something’s been altered.
Hashing in Action:
Hashing is essential for password security. Instead of storing passwords in plain text, systems store password hashes. During login, your typed password is hashed and compared to the stored hash. If they match, you gain access without revealing the actual password. Hashing also ensures data integrity by allowing systems to compare hashes before and after data transfer or storage, identifying any unauthorized changes. Additionally, hashing supports digital signatures, where a document’s hash is encrypted with the sender’s private key, allowing recipients to verify authenticity using the sender’s public key.
Encryption vs. Tokenization: Spotting the Differences
While encryption and tokenization both aim to protect data, they work in very different ways, each with pros and cons. Understanding the encryption and tokenization differences is key to choosing the right tool for the job.
Reversibility: Can You Get Back the Original Data?
Tokenization is designed to be reversible. You can get back the original data from a token by going through the tokenization system or vault. This is needed for things like processing payments, where you eventually need the real card details to complete the transaction. Encryption reversibility, however, depends on having the decryption key. Without it, encrypted data stays scrambled. This controlled reversibility is what makes encryption so good at keeping secrets.
Security and Speed: How Secure and How Fast Are They?
Tokenization is generally less secure than strong encryption. Its security depends heavily on keeping the token vault safe. If the vault is breached, tokens become useful to attackers. However, tokenization is generally faster than encryption. Creating and using tokens is quick and doesn’t use up many resources, making it efficient for high-speed processes. Encryption with strong algorithms offers very high security. Breaking it without the key is incredibly difficult. However, encryption can be slower and more resource-intensive, especially when dealing with lots of data. This can sometimes affect system performance.
Compliance and Rules: Meeting Regulatory Needs
Tokenization can be a big help in meeting data privacy rules like PCI DSS and GDPR. By reducing how much sensitive data you store and handle, it simplifies compliance and lowers the risk of fines. Encryption, on the other hand, is often a must for regulatory compliance, especially in healthcare and finance. Rules like HIPAA and GLBA require encryption to protect health and financial information.
In short, encryption is your go-to for strong confidentiality and security through complex algorithms and keys. Tokenization, on the other hand, is about minimizing data exposure and risk by using substitutes. The best choice depends on your specific security needs, how performance-sensitive your application is, and what regulations you need to follow.
Tokenization vs. Encryption: Not Cut from the Same Cloth
It’s a common mistake to think tokenization is the same as encryption. While both are about protecting sensitive data, they are fundamentally different in their approach and how they work. It’s important to understand why tokenization and encryption are not the same to use them correctly.
Tokenization is not encryption. Tokenization is data substitution; encryption is data transformation. Tokens are placeholders, while ciphertext is scrambled data that needs a key to unscramble. The reversal method differs significantly: tokenization is reversed by looking up the original data in a secure vault, whereas encryption is reversed using a cryptographic key.
Furthermore, tokenization doesn’t change the original data mathematically; it just replaces it. Encryption, in contrast, actually transforms the data into an unreadable form. Finally, tokenization security depends on keeping the token vault secure, while encryption security relies on the strength of the algorithm and keeping keys secret.
While tokenization vs encryption are both valuable for security, they aren’t interchangeable. Tokenization is best when you want to reduce data risk and exposure, like in payments and data masking. Encryption is the better choice when you need strong confidentiality and security, such as for secure communications and protecting stored data.
Tokenization vs Encryption vs Hashing: A Comparative Analysis
Let’s break down the core differences between tokenization, encryption, and hashing in a table for a clearer comparison across key aspects:
| Feature | Tokenization | Encryption | Hashing |
| Reversibility | Yes, via token vault | Yes, with decryption key | No, one-way function |
| Main Goal | Data substitution, minimize risk | Data confidentiality, secure communication | Data integrity, password security |
| How it Works | Replaces data with non-sensitive tokens | Transforms data into ciphertext | Creates a fixed-size hash value |
| Security Focus | Vault security is crucial | Key management and algorithm strength | Resistance to collisions, one-way nature |
| Performance | Generally fast | Speed varies by algorithm | Very fast |
| Best Used For | Payments, data masking | Data in transit/at rest, private comms | Passwords, verifying data integrity |
This table gives you a quick view of the distinctions between tokenization vs encryption vs hashing. Tokenization is about minimizing data and boosting speed, encryption is about strong confidentiality, and hashing is about ensuring data hasn’t been tampered with and securing passwords.
Choosing Your Security Shield: Tokenization, Encryption, or Hashing?
Picking the right data security method depends on what you’re trying to protect and why. Let’s look at when to use tokenization, encryption, or hashing in different situations.
Tokenization is ideal for payment processing and data masking. Consider it for Payment Card Industry (PCI) Compliance, as tokenization is essential for meeting PCI DSS standards, and securing credit card data in payment systems. By using tokens for card details, businesses drastically cut down on PCI scope and the chance of card data theft. Also, for masking data for testing and development, tokenization is great for hiding sensitive data in these environments. Using tokens instead of real data lets teams work with realistic data without risking exposure of actual sensitive information.
ℹ️In Short: “Tokenization is essential for PCI compliance and secure data masking, reducing the risk of data theft and enabling safe testing environments by replacing sensitive data with tokens.”
Encryption is best for secure data storage and transfer. For securing data at rest, encryption is vital for protecting stored data in databases, file systems, and cloud storage. It ensures that even if storage systems are breached, the data remains unreadable without decryption keys. For secure data in motion, encryption is key for securing data as it travels across networks, including the Internet. Technologies like TLS/SSL and VPNs use encryption to protect data moving between systems, preventing eavesdropping and interception.
ℹ️In Short: “Encryption is critical for securing data at rest and in motion, ensuring data remains unreadable during breaches and protected during transfers across networks.”
Hashing is suited for passwords and data checks. For password security, hashing is the top method for storing passwords securely. Hashing passwords before storage means that even if password databases are stolen, attackers can’t get usable passwords. For verifying data integrity, hashing is invaluable for ensuring data integrity, confirming that data hasn’t been altered. Hashes act as digital fingerprints, allowing systems to detect any unauthorized changes to data.
ℹ️In Short: “Hashing is the cornerstone of password security and data integrity, safeguarding passwords from theft and verifying data authenticity through unique digital fingerprints.”
Choosing between tokenization vs encryption vs hashing requires thinking about the data’s nature, the risks, performance needs, and any legal requirements. Often, the strongest approach is to use a mix of these methods, like combining tokenization and encryption for multi-layered security.
Weighing the Options: Pros and Cons of Each Method
Each security method has its own set of advantages and disadvantages, and understanding these trade-offs is key to making smart choices about which security tools to use.
Tokenization: Advantages and Disadvantages
Tokenization offers several advantages. It leads to a reduced data breach risk because tokens replace sensitive data, significantly reducing the risk of breaches, as even if tokens are stolen, they’re useless without the token vault. It provides simplified compliance, as tokenization can simplify meeting rules like PCI DSS and GDPR by limiting sensitive data handling. It also boasts fast performance, generally being quick and efficient for high-speed systems. Finally, it supports data minimization, helping reduce the amount of sensitive data businesses need to manage.
However, tokenization also has disadvantages. Its security is heavily dependent on vault security; a weak vault can undo all tokenization benefits. It adds complexity, as setting up and running a tokenization system can make data processes more complex. Lastly, its security scope is limited, being great for data at rest and in use, but less so for data in transit compared to encryption.
Encryption: Advantages and Disadvantages
Encryption’s advantages are significant. It provides top-tier security, with strong encryption offering very robust data protection, making unauthorized access extremely difficult. It ensures guaranteed confidentiality, being the best way to ensure data privacy, both when it’s moving and when it’s stored. Furthermore, it is often required for regulations, as encryption is frequently legally mandated to protect sensitive data.
The disadvantages of encryption include that it is resource intensive, as encryption can be demanding on systems, potentially slowing things down, especially with large data volumes. Key management is complex and critical; securely managing encryption keys is vital, and lost or compromised keys can lead to data breaches or loss. Finally, it can introduce performance impact, as encryption can add overhead, potentially slowing down data processing and transfers.
Hashing: Advantages and Disadvantages
Hashing offers the advantage of irreversible security. Hashing’s one-way nature is perfect for password security, as passwords can’t be recovered from hashes. It also provides high speed, being very fast, ideal for quick data checks and password verification. Finally, it ensures data integrity, reliably confirming data hasn’t been altered.
However, hashing’s disadvantages include its irreversible design; you can’t get the original data back from a hash, limiting its use for confidentiality where data recovery is needed. There is also a collision risk, though rare with strong algorithms, hash collisions are possible, potentially undermining data integrity in specific cases. Lastly, its security focus is limited, mainly for integrity and password security, not for broad data confidentiality like encryption.
Pro-Shield Tip: Maximizing Crypto Bank Safety with Tokenization & Encryption
In the fast-evolving world of crypto banking, distinguishing between legitimate platforms and potential scams is crucial. Ensuring maximum security involves more than just choosing a trustworthy platform it requires strong data protection techniques like tokenization and encryption.
First Step: Verify the Crypto Bank’s Legitimacy
- Check Regulatory Compliance: Ensure the platform is licensed and regulated by authorities like the SEC, FCA, or MAS.
- Assess Security Measures: Look for cold storage, multi-factor authentication (MFA), and end-to-end encryption to protect assets.
- Review Deposit Insurance & Terms: If a crypto bank claims to offer insurance, verify the provider and terms. Be cautious of vague claims.
- Test Customer Support: Unresponsive or slow support can indicate a lack of credibility. Legitimate platforms provide 24/7 assistance.
- Monitor Reviews & Community Sentiment: Read user experiences on independent forums, Trustpilot, and regulatory warning lists.
Second Step: Fortify Security with Tokenization & Encryption
To enhance the security of crypto bank transactions, employ tokenization and encryption together:
Tokenization replaces sensitive data (e.g., private keys, and account details) with randomized tokens, making them useless if breached.
Encryption ensures that even if data is stolen, it remains unreadable without the decryption key.
Third Step: Smart Investment & Risk Management
- Never store all assets in one place: use hardware wallets, exchange wallets, and multi-sig accounts.
- Be skeptical of “guaranteed” high returns: scams often promise risk-free profits.
- Use strong authentication methods: enable 2FA or biometrics for additional protection.
By combining tokenization, encryption, and proper due diligence, you can confidently navigate the crypto banking space with reduced risks and stronger asset protection.
Tokenova: Your Data Security Innovator
In today’s complex security landscape, you need more than just tools you need a partner. Tokenova leads the way in tokenization and encryption solutions, tailored to fit your unique business challenges. Our experts offer end-to-end services, from initial security assessments to custom strategy design, smooth implementation, and continuous support.
Unlock the Power of Tokenization with Tokenova:
- Slash PCI scope and dramatically reduce data breach threats.
- Enable secure, streamlined payment processing and advanced data analytics.
- Simplify your path to full compliance with stringent data privacy regulations.
Fortify Your Defenses with Tokenova Encryption Solutions:
- Safeguard sensitive data in motion and at rest with state-of-the-art encryption.
- Guarantee data confidentiality and build lasting customer trust.
- Effortlessly meet and exceed industry-standard regulatory demands.
Conclusion
In summary, tokenization, encryption, and hashing are vital tools in the world of cybersecurity. Each has its own strengths, and they aren’t meant to replace each other. Understanding the differences between tokenization vs encryption vs hashing is key to making smart security choices.
Tokenization is excellent for cutting down data risks and boosting efficiency, perfect for payments and data masking. Encryption is your best bet for strong confidentiality, securing data everywhere it lives and moves. Hashing is crucial for ensuring data integrity and securing passwords. For the strongest defense, think about a hybrid approach that uses both tokenization and encryption for a truly comprehensive security strategy.
By carefully using these methods, businesses can create strong, multi-layered security, protect sensitive information, build customer confidence, and confidently navigate the ever-changing world of data privacy rules. It’s not about choosing just one; it’s about knowing each tool and how to combine them for the best possible data defense.
Key Technical Points
- Tokenization replaces real data with tokens, is reversible, and fast, best for minimizing data exposure.
- Encryption scrambles data with keys, is reversible with the key, very secure, and best for confidentiality.
- Hashing creates irreversible fingerprints of data, is one-way and very fast, and best for integrity and passwords.
- Reversibility: Tokenization and Encryption are reversible; Hashing is not.
- Security Focus: Tokenization vaults, Encryption keys, Hashing collision resistance.
- Hybrid Security: Tokenization + Encryption = strongest protection.
Can tokenization protect against insider threats effectively?
Yes, tokenization can significantly mitigate insider threats. By replacing sensitive data with tokens, even if an insider breaches systems holding these tokens, they are blocked from accessing the genuine sensitive information. The crucial token vault, designed with strict access protocols and continuous monitoring, remains the key safeguard. This multi-layered security significantly curtails the danger of data theft by both malicious and careless insiders.
How critical is encryption key management to data security?
Encryption key management is not just important it’s the cornerstone of data security when using encryption. Weak key management can undermine even the strongest encryption. Secure key practices include generating strong keys, secure storage, controlled distribution, regular rotation, and immediate revocation when necessary. Implementing robust key management systems and adhering to strict protocols are essential to protect encryption keys throughout their lifecycle, ensuring data confidentiality and preventing unauthorized access.
Are there performance limitations when hashing very large datasets?
While hashing is renowned for its speed and efficiency, processing extremely large datasets can introduce performance considerations. The computational demand of generating hash values for massive data volumes can consume considerable processing power and time. However, for the vast majority of applications, the performance impact of hashing is minimal. For exceptionally large datasets, techniques such as parallel hashing and algorithm optimization can effectively mitigate potential performance bottlenecks, maintaining efficiency even at scale.
When is data masking preferred over tokenization or encryption?
Data masking emerges as the preferred technique over tokenization or encryption when the primary goal is to create realistic, non-sensitive data replicas for non-production environments like testing and development. Masking excels in scenarios where the original data is not needed, and the focus is on data minimization and creating functional, yet anonymized datasets. Techniques such as redaction, substitution, and shuffling within data masking ensure that datasets mimic production data in format and structure but crucially lack actual sensitive information. This approach is particularly advantageous when sharing data with external parties or utilizing data in less secure environments where reversibility is unnecessary, and risk reduction is paramount.