Blockchain’s rapid evolution demands robust defenses, and understanding how to improve blockchain security is more critical than ever. As digital assets and decentralized systems expand, so do the threats targeting them. This guide provides a deep dive into multi-layered security strategies—from protocol to user practices—that can help organizations and developers safeguard their blockchain networks.
In this article we teach you proven methods, actionable strategies, and emerging technologies to address vulnerabilities effectively while ensuring system integrity.
First, Understanding Blockchain Security Layers
Blockchain security is a multifaceted discipline that involves safeguarding each distinct layer of the system. In this section, we break down the overall architecture into its core layers—protocol, network, application, and user—highlighting how vulnerabilities at each level can impact the entire ecosystem. A clear understanding of these layers is the first step in developing comprehensive security measures.
Protocol Layer Security: Consensus and Cryptography

At the protocol layer, the integrity of the blockchain is maintained through consensus mechanisms and cryptographic techniques. This core layer ensures that every transaction is securely validated and recorded.
Robust Consensus Mechanisms
Selecting the right consensus algorithm is essential. Traditional Proof of Work (PoW) provides security against some attacks but risks centralization, whereas Proof of Stake (PoS) and Delegated Proof of Stake (DPoS) offer efficiency with different trade-offs. Hybrid models combining PoS with Byzantine Fault Tolerance can reduce vulnerabilities and improve overall security.
Strong Cryptography
Cryptographic primitives such as hash functions, digital signatures, and encryption algorithms form the backbone of blockchain security. Regular cryptographic audits and the shift toward quantum-resistant algorithms are proactive ways to stay ahead of threats.
⏹️DecentraTip: “Quantum-resistant algorithms” are still largely in the research phase and not yet widely adopted. Most blockchain systems still rely on traditional cryptographic methods (e.g., SHA-256, ECDSA), and the transition to quantum-resistant cryptography is a long-term goal.
Formal Verification and Auditing
Mathematical proofs and thorough audits ensure that protocol code behaves as intended, identifying potential vulnerabilities that traditional testing may miss.
Network Layer Security: Node Security, Communication, and Infrastructure
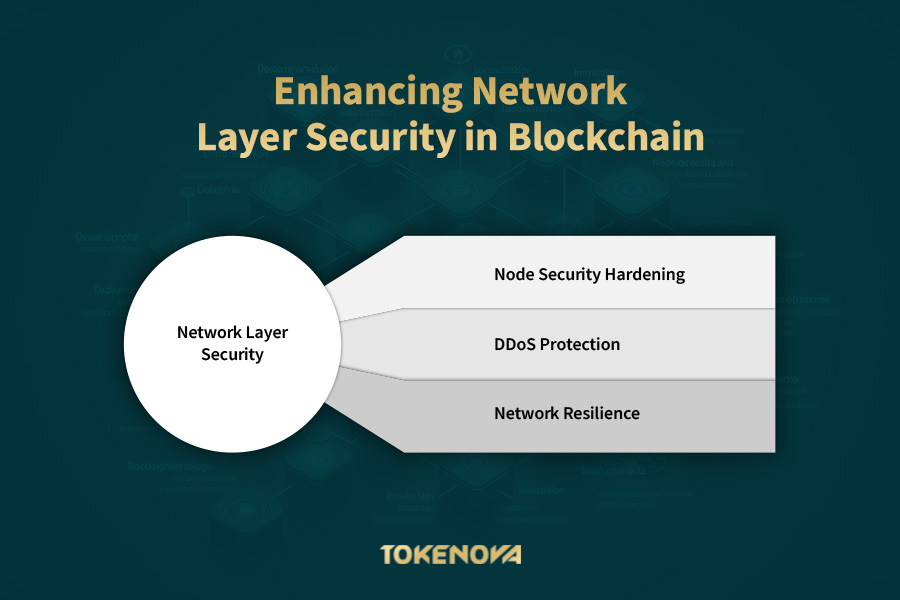
The network layer is responsible for the secure communication between nodes and the overall stability of the blockchain. Understanding and mitigating risks at this level is vital for maintaining system integrity.
Node Security Hardening
Implementing best practices for server security—such as regular patching, proper configuration management, and minimizing unnecessary services—can significantly reduce the risk of attacks.
DDoS Protection and Network Resilience:
Distributed Denial of Service (DDoS) attacks can cripple network communication. Blockchain networks can remain operational even under attack by geographically dispersing nodes and leveraging advanced DDoS mitigation services. For example, some networks absorbed attacks during a period when illicit crypto volume declined by 24% in 2024.
Secure Communication Channels
Encrypting data in transit using protocols like TLS prevents man-in-the-middle attacks, ensuring that node communications remain confidential and tamper-proof.
Application Layer Security: Smart Contracts, dApps, and User Interfaces

The application layer includes smart contracts and decentralized applications (dApps), where business logic is executed. Securing this layer is crucial because vulnerabilities here can directly lead to significant financial losses.
Secure Smart Contract Development Practices
Developers must adhere to secure coding guidelines and leverage automated vulnerability scanning tools. Techniques like the “check-effects-interactions” pattern help prevent common pitfalls such as re-entrancy attacks.
Smart Contract Audits and Bug Bounties
Independent audits and incentivized bug bounty programs ensure that vulnerabilities are identified and resolved before they can be exploited.
Securing dApp Interfaces
Robust input validation, strong authentication, and regular security assessments are essential to protect user interfaces from web-based attacks such as cross-site scripting and injection.
User-Side Security: Wallets, Key Management, and User Practices
The human element is often the weakest link in security. User-side vulnerabilities, particularly in wallet security and key management, can lead to irrevocable asset loss.
Wallet Security and Key Management
Modern blockchain-specific key management systems (KMS) provide secure key generation, storage, and distribution. With the permanent loss of assets tied to lost keys, employing robust KMS solutions is indispensable.
Multi-Factor Authentication and User Education
Educating users on best practices—including the use of multi-factor authentication (MFA) and secure backup procedures—is key to ensuring overall system security. Additionally, empowering users with knowledge on how to improve blockchain security through proper practices is vital for a secure ecosystem.
Improving Protocol Layer Security: Fortifying the Core

A robust protocol layer is essential for a secure blockchain network. This section focuses on advanced strategies to fortify the core components of blockchain systems and explains in detail how to improve blockchain security from the inside out.
Robust Consensus Mechanisms
Consensus mechanisms are the heart of blockchain technology, ensuring that all network participants agree on transaction validity.
Evaluating Consensus Options
While PoW has been a long-standing method, its high energy consumption and potential centralization risks make it less favorable in today’s environment. PoS and DPoS offer a more sustainable and scalable alternative, although they must be carefully designed to avoid concentration of power. Combining these with hybrid models that incorporate Byzantine Fault Tolerance can create a more secure consensus environment. Such integration is critical for understanding how to improve blockchain security at the protocol level, mitigating vulnerabilities like 51% attacks effectively.
Network Partition Resistance
Resilience against network partitions is achieved through robust communication protocols. Secure gossip protocols ensure rapid and reliable data propagation across nodes even when portions of the network are compromised. These mechanisms are indispensable in developing strategies on how to improve blockchain security during adverse network conditions.
Strong Cryptography and Key Management
Ensuring that cryptographic systems remain robust is pivotal to maintaining blockchain security.
Cryptographic Audits and Upgrades
Continuous auditing of cryptographic protocols is essential. As threats evolve, so must the algorithms that underpin blockchain security. Transitioning to quantum-resistant algorithms ensures that the blockchain remains secure in the face of future quantum computing advancements. This proactive approach is one of the most effective methods on how to improve blockchain security.
Enhanced Key Management Solutions
Integrating modern KMS and Hardware Security Modules (HSMs) significantly mitigates the risk of key compromise. By isolating cryptographic keys from potential software vulnerabilities, these systems reduce the likelihood of unauthorized access.
Formal Verification and Auditing
Mathematical precision in verifying blockchain protocols can eliminate many potential vulnerabilities before they manifest.
⏹️DecentraTip: Formal verification is highly effective but can be resource-intensive and may not catch all vulnerabilities, especially in complex systems.
Comprehensive Testing through Formal Verification
Formal verification involves creating mathematical models of blockchain protocols to prove their security under all possible conditions. This rigorous process, when combined with independent security audits, provides a level of assurance unmatched by conventional testing methods. By integrating these advanced techniques, developers can clearly see how to improve blockchain security in their core protocols and ensure that the system operates flawlessly even under stress.
Enhancing Network Layer Security: Defending the Infrastructure
The network layer is the critical communication infrastructure of any blockchain system. Its security is vital for maintaining both data integrity and system availability. This section details advanced techniques on how to improve blockchain security in the network environment.
- Node Security Hardening
Securing individual nodes is the first step toward a robust network defense.
Best Practices for Node Protection
Nodes must be regularly updated and hardened through proper configuration management. Minimizing unnecessary services reduces the potential attack surface. Specialized intrusion detection systems, tailored to monitor blockchain-specific traffic, can rapidly identify suspicious behavior. Physical security measures, such as securing data centers and ensuring redundancy, further enhance node protection. These measures are integral in demonstrating actionable insights on how to improve blockchain security at the network level.
Redundancy and Geographic Distribution
Distributing nodes across multiple geographic locations not only improves load balancing but also minimizes the risk of localized disruptions. This geographical redundancy is essential to ensuring that the network remains operational even if certain regions face cyberattacks or natural disasters.
- DDoS Protection and Network Resilience
Maintaining continuous network availability is paramount for blockchain operations.
Mitigating DDoS Attacks
Advanced DDoS mitigation techniques involve using cloud-based solutions to filter out malicious traffic before it reaches the blockchain network. By integrating these services, organizations can maintain uninterrupted service even during high-volume attacks. This approach has proven effective, as demonstrated during periods of increased threat activity, and is a key factor in understanding how to improve blockchain security.
Strengthening Network Resilience
Implementing redundant network architectures and ensuring that communication protocols can withstand partial network failures are essential. Secure routing protocols and load-balancing mechanisms distribute traffic efficiently, ensuring that the network remains resilient under various attack vectors.
- Secure Communication Channels and Encryption
Data integrity and confidentiality depend heavily on secure communication.
Implementing Strong Encryption Protocols
Encrypting all inter-node communications using standards like TLS ensures that data remains secure during transit. Advanced features such as certificate pinning and secure key exchanges add extra layers of protection.
Ongoing Security Assessments
Regular assessments of communication channels help identify and patch any vulnerabilities in the encryption protocols. These evaluations are crucial in long-term strategies on how to improve blockchain security, ensuring that the network adapts to new threats as they emerge.
Strengthening Application Layer Security: Securing Smart Contracts and dApps
The application layer is where business logic meets execution, making it a prime target for attackers. Detailed strategies here are essential in showcasing how to improve blockchain security at the point of interaction between code and user.
- Secure Smart Contract Development Practices
Smart contracts are inherently risky if not developed with strict security protocols.
Adherence to Secure Coding Guidelines
Developers must follow best practices such as the “check-effects-interactions” pattern to prevent vulnerabilities like re-entrancy attacks. Rigorous testing—comprising unit, integration, and scenario-based tests—is mandatory. Tools that automate vulnerability scanning further enhance the reliability of these contracts
Integration of AI-Enhanced Tools
Advanced AI systems now play a role in detecting anomalies within smart contract code. These tools can analyze code faster and more thoroughly than traditional methods, offering significant improvements in identifying potential vulnerabilities before they can be exploited.
- Smart Contract Audits and Bug Bounties
Pre-deployment and ongoing security evaluations are crucial. This is commonly done through these two:
Comprehensive Security Audits
Engaging reputable third-party firms to audit smart contracts ensures that vulnerabilities are addressed before launch. These audits, combined with formal verification methods, provide a multi-layered defense that clearly outlines how to improve blockchain security at the application level.
Effective Bug Bounty Programs
Bug bounty initiatives incentivize external security researchers to find and report issues, creating an additional safety net that continuously monitors and improves contract security.
- dApp Security Best Practices
Decentralized applications require robust security frameworks to protect users and data.
Securing Front-End Interfaces
dApp interfaces must implement stringent input validation, strong authentication, and secure session management to prevent traditional web vulnerabilities such as cross-site scripting and injection attacks.
Transparent Security Practices
By maintaining open-source codebases, clear security policies, and consistent updates, organizations not only build trust with their users but also foster a community-based approach to identifying potential vulnerabilities, thereby reinforcing strategies on how to improve blockchain security.
Emerging Technologies and Trends in Blockchain Security
As the blockchain landscape evolves, so too do the methods of defense. This section explores cutting-edge technologies and trends that are redefining how to improve blockchain security and prepare networks for future challenges.

AI and Machine Learning for Security Monitoring and Threat Detection
Artificial intelligence has become indispensable in modern cybersecurity.
Advanced Anomaly Detection
AI-driven models are now capable of processing vast datasets in real time, identifying anomalous patterns that signal potential security breaches. AI-driven threat detection systems, such as Falcon, identify irregularities up to five times faster than conventional methods, making them a crucial element in any comprehensive strategy on how to improve blockchain security.
Predictive Analytics
Leveraging machine learning for predictive analytics allows systems to forecast potential threats before they manifest. By integrating these insights, blockchain networks can proactively adjust defenses, effectively demonstrating a forward-thinking approach to how to improve blockchain security.
Zero-Knowledge Proofs for Enhanced Privacy and Security
Zero-knowledge proofs (ZKPs) offer an innovative solution for balancing transparency with confidentiality.
Maintaining Confidentiality without Compromise
ZKPs allow one party to verify the accuracy of information without revealing the information itself. This approach is particularly beneficial in scenarios where data privacy is paramount, thus providing a novel method on how to improve blockchain security while ensuring transaction verifiability.
Post-Quantum Cryptography for Future-Proofing Blockchain Security
Quantum computing represents a significant future threat to traditional cryptographic algorithms.
Transitioning to Quantum-Resistant Algorithms
Research into lattice-based, hash-based, and multivariate cryptographic methods is ongoing. Implementing these advanced algorithms now is a proactive measure on how to improve blockchain security, ensuring that blockchain systems remain secure in a post-quantum world.
Hybrid Cryptographic Systems
Integrating current cryptography with quantum-resistant solutions creates a bridge that protects legacy systems while preparing for future challenges. Such hybrid models are essential for long-term security planning.
Hardware Security Modules (HSMs) for Enhanced Key Protection
Hardware Security Modules (HSMs) provide a dedicated, tamper-resistant environment for key management.
Isolating Critical Keys
By storing cryptographic keys in HSMs rather than software-based solutions, organizations drastically reduce the risk of key compromise. Reports indicate that HSMs can lead to fewer key compromise incidents, demonstrating a practical example of how to improve blockchain security through advanced hardware solutions.
Integration and Management
Effective integration of HSMs with blockchain networks and Key Management Systems (KMS) is vital. This integration not only secures the keys but also streamlines key management processes, enhancing overall system security.
Key Takeaways
- Layered Security Approach: Effective blockchain security relies on a multi-layered defense strategy covering protocol, network, application, and user aspects.
- Robust Consensus & Cryptography: Strengthening core components with robust consensus mechanisms, advanced cryptography, and formal verification is essential to demonstrate how to improve blockchain security.
- Network Resilience: Hardening node security, mitigating DDoS attacks, and ensuring encrypted communication are key steps in maintaining a resilient blockchain network.
- Application Security: Secure coding practices, rigorous audits, and proactive bug bounty programs safeguard smart contracts and dApps, reducing vulnerabilities significantly.
- User Empowerment: Educating users on secure practices, implementing modern key management solutions, and using multi-factor authentication play a crucial role in preventing breaches.
- Emerging Technologies: Integrating AI for threat detection, zero-knowledge proofs for privacy, and post-quantum cryptography are forward-thinking strategies that further enhance blockchain security.
Conclusion
A proactive, multi-layered approach is essential in determining how to improve blockchain security effectively. By securing every level—from protocol and network to application and user practices—organizations can build resilient blockchain ecosystems. Embracing emerging technologies such as AI, zero-knowledge proofs, and post-quantum cryptography further bolsters defenses. With continuous improvement and rigorous security protocols, stakeholders can safeguard digital assets and maintain system integrity in an ever-evolving threat landscape.