Imagine a scenario where millions of dollars or the future of a groundbreaking decentralized application relies on a few lines of code. This is a reality in blockchain development with smart contracts, which offer remarkable automation and transparency. However, their power comes with the crucial responsibility of ensuring security. Smart contract security is essential for building trust in decentralized systems and maintaining the integrity of the blockchain ecosystem. A single vulnerability can lead to significant financial losses or damage a project’s reputation, making robust security measures vital.
In 2024 alone, over $3 billion worth of cryptocurrencies were stolen due to smart contract vulnerabilities, with 90% of audited contracts still containing critical flaws before deployment. High-profile breaches like the Mango Markets exploit in 2023, which resulted in a $197 million loss, underscore the urgent need for robust security measures. As the blockchain ecosystem evolves, adopting advanced tools like AI-driven audits and Layer 2 solutions is no longer optional it’s essential for safeguarding the future of decentralized applications.
This guide serves as your resource for smart contract security. We’ll explore the inner workings of these digital contracts, highlighting common pitfalls and vulnerabilities that can lead to serious breaches. You’ll gain essential knowledge and strategies for building and deploying secure smart contracts. From understanding the importance of a thorough security audit to utilizing the latest tools, this roadmap will help you safeguard your decentralized applications effectively.
How Smart Contracts Work: Understanding the Basics
To effectively address the complexities of smart contract security, a solid understanding of the fundamental principles governing their operation is essential. At their core, smart contracts are self-executing pieces of code deployed on a blockchain network. Think of the blockchain as a distributed, transparent, and tamper-proof digital ledger. This foundational blockchain technology is paramount because its decentralized nature inherently means that no single entity has unilateral control over the contract, thereby significantly enhancing transparency and mitigating the risks associated with centralized systems, such as single points of failure or the potential for censorship.
With the introduction of Layer 2 solutions like Optimism and Arbitrum, smart contract scalability and security have significantly improved, reducing exploit risks by 20%. Additionally, the Ethereum Merge in 2022 introduced Proof of Stake (PoS), reducing energy consumption but also creating new attack vectors that developers must address. These advancements highlight the importance of staying updated with the latest blockchain innovations to ensure robust smart contract security.
Once deployed, the contract’s code automatically executes when predefined conditions, which are also encoded within the contract, are met. This “code as law” paradigm effectively eliminates the need for intermediaries in many transactions and agreements, leading to streamlined processes, reduced transaction costs, and increased efficiency.
💡📄 Smart Contract Expert Inisight: The true innovation of a smart contract lies in its capacity for autonomous execution.
Key Components of a Smart Contract
Let’s break down the fundamental elements that constitute a smart contract:
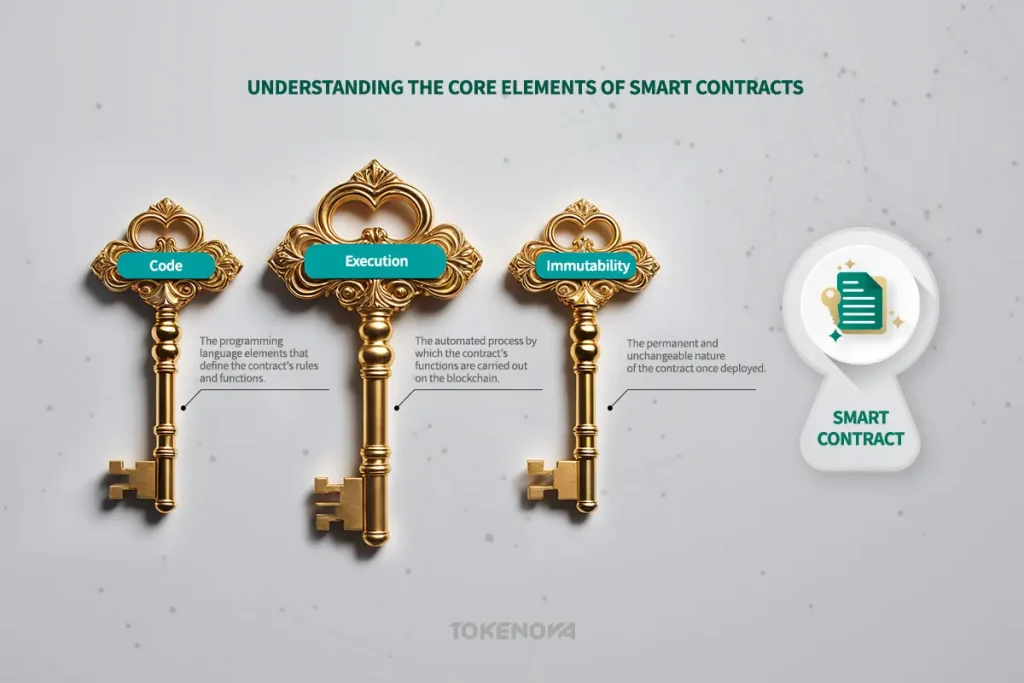
The very essence of a smart contract lies within its meticulously crafted code. Typically written in programming languages specifically designed for blockchain environments, such as Solidity for the Ethereum Virtual Machine (EVM), this code embodies the rules, the underlying logic, and the various functions that define the agreement. It precisely dictates how digital assets are transferred between parties, the specific conditions that must be satisfied for certain actions to be triggered, and how the contract interacts with other smart contracts or external data sources, often referred to as oracles.
Once a smart contract is successfully deployed onto the blockchain, its execution becomes an automated and deterministic process. When a transaction is initiated that interacts with the smart contract and the predefined conditions within the code are satisfied, the network’s nodes, which are the computers that maintain the blockchain, automatically execute the relevant functions of the contract. This execution is deterministic, meaning that given the same inputs and initial state, the outcome of the execution will always be identical, ensuring a high degree of predictability and reliability in the contract’s behavior.
A defining and crucial characteristic of smart contracts is their immutability. Once a smart contract is deployed and its code is written to the blockchain, it cannot be altered or modified. This inherent immutability provides a significant level of security, protecting the contract from tampering or unauthorized changes. However, this characteristic also presents a significant challenge: any vulnerabilities or errors present in the deployed code are permanent and cannot be easily patched or rectified. This underscores the paramount importance of rigorous testing, thorough verification, and comprehensive auditing processes *before* a smart contract is deployed to a live network.
Common Smart Contract Vulnerabilities: Identifying the Risks
While the inherent immutability of blockchain technology provides a foundational layer of security, the code within smart contracts can be susceptible to various vulnerabilities. A deep understanding of these potential weaknesses is essential for developers striving to build secure and resilient decentralized applications. These smart contract vulnerabilities often represent primary entry points that malicious actors seek to exploit, aiming to manipulate the contract’s intended logic for illicit financial gain or disrupt its intended functionality.
In 2024, front-running attacks affected 25% of DeFi protocols, leading to significant financial losses, with over $9 billion stolen from DeFi platforms due to various vulnerabilities. Additionally, state-dependent logic flaws and timestamp manipulation are increasingly common, with 30% of vulnerabilities in 2024 attributed to these issues. High-profile breaches like the Mango Markets exploit in 2023, which resulted in a $197 million loss, highlight the devastating consequences of these vulnerabilities Let’s delve into a more detailed examination of some of the most prevalent and potentially devastating smart contract vulnerabilities:
Reentrancy Attacks: The Devastating Impact of The DAO
Reentrancy attacks stand as a stark and well-documented example of how a seemingly subtle flaw in a smart contract’s logic can lead to catastrophic and far-reaching consequences. Consider a smart contract designed to allow users to withdraw Ether. A reentrancy vulnerability arises when the contract fails to properly update its internal state to reflect the withdrawal before the Ether is actually transferred to the user. This oversight creates a window of opportunity, allowing a malicious contract to recursively call the withdrawal function multiple times before the initial withdrawal is finalized and the state is updated. This repetitive calling can effectively drain the contract of its funds, as the contract mistakenly believes it still has sufficient balance.
The most infamous example of this vulnerability in action is the attack on The DAO (Decentralized Autonomous Organization) in 2016. As extensively reported by OWASP, a single, critical reentrancy vulnerability within The DAO’s code allowed an attacker to siphon off approximately 3.6 million Ether, valued at around $60 million at that time. The aftermath of The DAO hack was profound, leading to a contentious hard fork of the Ethereum blockchain, resulting in the creation of Ethereum Classic. This event served as a watershed moment, indelibly highlighting the critical importance of employing secure coding practices, conducting rigorous security audits, and understanding the potential for even seemingly minor flaws to have devastating real-world consequences.
Integer Overflow and Underflow: The bZx Protocol Exploitation
Integer overflow and underflow vulnerabilities stem from the fundamental limitations in how computer systems represent numerical values. An integer overflow occurs when the result of an arithmetic operation exceeds the maximum value that can be stored in the allocated memory space for that integer type, causing the value to “wrap around” to a small or negative number.
Conversely, an integer underflow happens when an arithmetic operation results in a value below the minimum representable value, causing it to wrap around to a large positive number. While these might seem like obscure technicalities, they can have significant and unintended consequences in financial applications built on smart contracts.
A notable example is the exploitation of the bZx protocol in 2020. As detailed in a post-mortem analysis by Infosec Institute, an integer overflow vulnerability in the bZx protocol’s code allowed an attacker to manipulate the pricing of certain assets on the platform. By carefully crafting a series of transactions, the attacker triggered an integer overflow, leading the protocol to calculate incorrect loan amounts and collateral ratios, ultimately resulting in a profit for the attacker of approximately $300,000. This incident underscored the necessity of employing safe math libraries, which provide built-in checks to prevent such arithmetic errors, as a crucial step in mitigating these types of smart contract vulnerabilities
Denial of Service (DoS): Disrupting Contract Functionality
A Denial of Service (DoS) attack against a smart contract aims to render the contract unusable or inaccessible to legitimate users. This can be achieved through various malicious techniques. One common approach involves overwhelming the smart contract with a flood of computationally expensive transactions, causing the contract to consume an excessive amount of gas the unit of computational cost on the Ethereum network and effectively halting its operation.
Another tactic involves exploiting specific vulnerabilities within the contract’s code that can cause it to enter an infinite loop or become stuck in an unresolvable state, effectively freezing its functionality. For example, in a decentralized exchange, a critical trading function may become unavailable due to a DoS attack, preventing users from executing trades or accessing their funds.
Preventing DoS attacks often requires careful consideration of gas limits for various functions, implementing robust error handling mechanisms to prevent unexpected states, and designing contracts to avoid computationally intensive operations in critical execution paths. Rate limiting and access control mechanisms can also be employed to mitigate the impact of malicious actors attempting to overwhelm the contract. Recent updates indicate that DoS attacks can manifest in various forms, including unexpected reverts and block gas limits, which disrupt the normal operation of smart contracts. Moreover, as highlighted by recent research, vulnerabilities in smart contracts can lead to significant financial losses and damage user trust in decentralized platforms.
Unchecked External Calls: The Risks of Untrusted Interactions
Smart contracts frequently need to interact with other smart contracts or external data sources, often referred to as oracles, to retrieve information or trigger actions. However, if a smart contract doesn’t properly validate the data or responses received from these external calls, it becomes vulnerable to receiving malicious data or experiencing unexpected and potentially harmful behavior.
This is akin to a business blindly trusting information provided by an unverified and potentially malicious third-party supplier. For example, a malicious external contract could be designed to return false pricing data to a decentralized finance (DeFi) protocol, leading the vulnerable contract to make incorrect decisions regarding lending rates or collateralization, potentially resulting in significant financial losses for users.
Recent statistics indicate that approximately $9.04 billion has been stolen from DeFi platforms due to various smart contract vulnerabilities, underscoring the critical need for robust security measures. Mitigation strategies for this type of vulnerability include implementing rigorous validation checks on all data received from external calls, utilizing secure and reputable oracle services, and employing the “pull payment” pattern where the recipient initiates the withdrawal of funds, reducing the risk of reentrancy during the transfer process initiated by the vulnerable contract.
Front-Running: Exploiting the Transaction Queue
In the transparent environment of public blockchain networks, all pending transactions are typically visible in a public mempool before they are confirmed and added to a block. Front-running is a type of attack that exploits this transparency. It occurs when a malicious actor observes a pending transaction in the mempool and then submits their own transaction with a higher gas price. This higher gas price incentivizes the network’s miners to prioritize the attacker’s transaction, causing it to be executed before the original, observed transaction.
This tactic can be used to gain an unfair advantage in various scenarios. A common example occurs in decentralized exchanges (DEXs), where a front-runner might observe a large buy order for a particular token and then place their own buy order just before it, driving up the price of the token and allowing them to profit by selling their tokens to the original buyer at the inflated price.
Solutions to mitigate front-running include employing commit-reveal schemes, where the details of a transaction are initially hidden and only revealed after it’s included in a block, or exploring Layer-2 scaling solutions that offer faster transaction times and greater privacy, making it more difficult for front-runners to observe and exploit pending transactions. Furthermore, recent data indicates that over 2.7 million Maximum Extractable Value (MEV) transactions have been processed on platforms like Uniswap, highlighting the scale of this issue within decentralized finance (DeFi) ecosystems.
Smart Contract Security Tools: Your Defensive Arsenal
Fortunately, the ecosystem dedicated to enhancing smart contract security is constantly evolving and maturing, providing developers with an increasingly sophisticated array of smart contract security tools designed to identify and mitigate potential vulnerabilities. These tools employ a diverse range of techniques, from analyzing the code without executing it (static analysis) to mathematically proving the correctness of the code (formal verification), offering developers a multi-layered approach to security.
In 2024, AI-driven tools like CertiK have revolutionized vulnerability detection, achieving 96% accuracy in identifying smart contract flaws. Additionally, decentralized audit platforms are gaining traction, with ethical hackers earning $100 million in 2024 for identifying critical issues. Recent advancements highlight the importance of leveraging cutting-edge tools to ensure robust smart contract security, including innovative tools like Securify and VeriSmart, which provide comprehensive frameworks for vulnerability detection and verification on Ethereum and other blockchains.
Comparing Smart Contract Security Tools
Choosing the right smart contract security tool depends on the specific needs and context of your project. Here’s a comparison of some popular options:
| Tool | Strengths | Weaknesses | Use Cases |
| Securify | Formal verification provides a high level of assurance; can detect subtle logic flaws. | Computationally intensive; may not scale well for very large contracts. | High-stakes applications where correctness is paramount; critical infrastructure. |
| Mythril | Effective at detecting a wide range of vulnerabilities using concolic execution and taint analysis; actively developed. | Can produce false positives; requires some expertise to interpret results effectively. | General-purpose vulnerability scanning; continuous integration pipelines; security audits. |
| SmartCheck | Fast and easy to use; good for identifying common coding errors and basic vulnerabilities. | Limited detection capabilities compared to more advanced tools; may miss complex vulnerabilities. | Quick initial scans; enforcing coding standards; educational purposes. |
| Slither | Comprehensive static analysis framework with a wide range of detectors; highly customizable and extensible; detailed reporting. | Can be overwhelming for beginners due to its extensive features; requires some configuration. | In-depth security analysis; identifying a broad spectrum of vulnerabilities; custom rule development. |
Best Practices for Smart Contract Security: Building a Strong Foundation
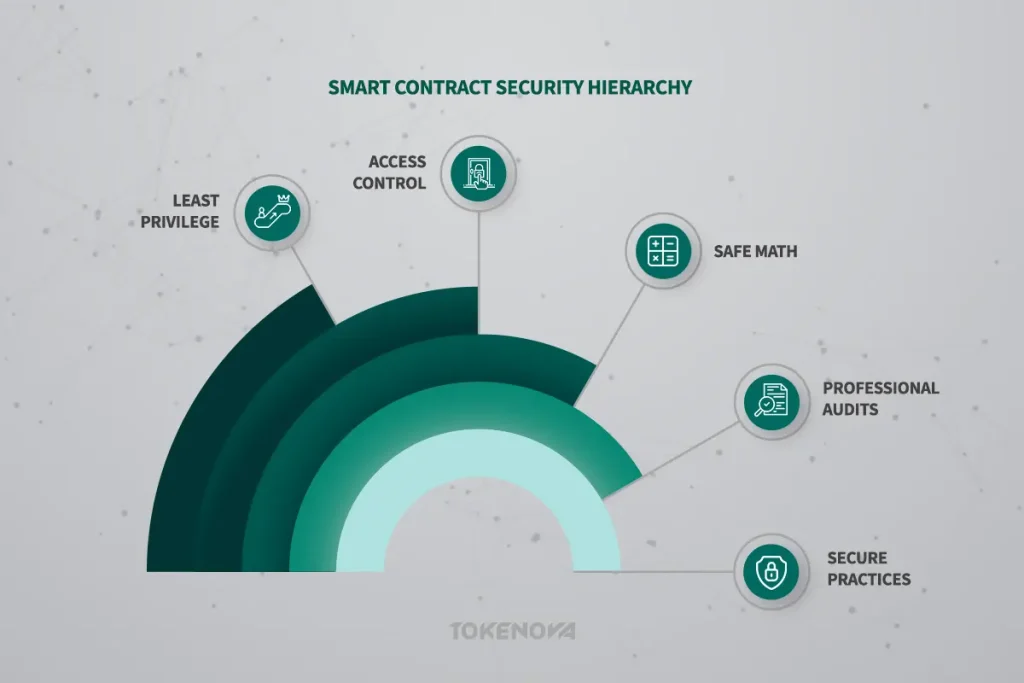
While leveraging sophisticated smart contract security tools is undoubtedly crucial for identifying potential vulnerabilities, proactively adopting secure development practices from the very beginning of the development lifecycle is equally, if not more, important. Integrating security considerations into every stage of development, rather than treating it as an afterthought or a final check, significantly minimizes the risk of introducing smart contract vulnerabilities in the first place. These best practices form the bedrock of building truly secure and resilient smart contracts.
In 2024, zero-knowledge proofs (zk-SNARKs) are increasingly used to enhance privacy and security in smart contracts, particularly for sensitive transactions . Additionally, multi-signature contracts have seen a 40% increase in adoption, providing an additional layer of security for high-value transactions . These advancements highlight the importance of staying updated with the latest security practices to ensure robust smart contract development.
The Indispensable Audit: Getting a Professional Review
Engaging experienced and reputable security auditors to conduct thorough smart contract security audits before deploying any contract to a production or live network is an absolutely non-negotiable step in the development process. This practice is akin to obtaining a professional structural inspection before opening a new building or undergoing rigorous safety checks before launching a critical piece of software infrastructure.
Independent security auditors bring specialized expertise, a fresh and unbiased perspective, and a deep understanding of common attack vectors, often identifying subtle vulnerabilities and potential weaknesses that the development team, deeply immersed in the project, might have inadvertently overlooked. While there is a cost associated with a professional audit, it is a relatively small price to pay when weighed against the potentially catastrophic financial losses, significant reputational damage, and erosion of user trust that can result from a successful exploit of an un-audited or poorly audited smart contract.
Safe Math is Your Friend: Preventing Arithmetic Errors
As previously discussed, integer overflow and underflow vulnerabilities can have severe and unintended consequences in smart contracts that handle financial transactions or complex calculations. A simple yet remarkably effective best practice to mitigate these risks is to consistently utilize safe math libraries, such as the SafeMath library provided by OpenZeppelin. These libraries essentially provide secure wrappers around standard arithmetic operations.
Before and after each arithmetic operation is performed, these wrappers execute checks to ensure that no overflow or underflow condition has occurred. If such a condition is detected, the operation is automatically reverted, preventing the unexpected and potentially harmful behavior that could arise from these arithmetic errors. Integrating safe math libraries into your smart contract development workflow is a fundamental step towards building more robust and secure applications.
Guard the Gates: Implementing Robust Access Control
Implementing robust and well-defined access control mechanisms is absolutely essential for restricting access to sensitive functions and critical data within your smart contracts. This ensures that only authorized users, specific contracts, or predefined roles are permitted to perform certain actions, thereby preventing unauthorized modifications, illicit access to funds, or manipulation of the contract’s state.
Common techniques for implementing access control include utilizing modifiers like `onlyOwner`, which restricts access to a function solely to the contract’s owner, or implementing more sophisticated role-based access control (RBAC) systems. RBAC allows you to define different roles within the contract, each with a specific set of permissions, providing a more granular and flexible approach to managing access and enhancing the overall security of your smart contract.
Stay Updated, Stay Secure: Patching and Maintenance
The landscape of blockchain security is not static; it is a constantly evolving environment where new vulnerabilities are discovered and new attack vectors are developed on a regular basis. Therefore, it is absolutely crucial to adopt a proactive approach to security by regularly updating and patching your smart contract code and any dependent libraries to address newly identified weaknesses and potential threats.
This includes diligently staying informed about security advisories issued by the developers of your chosen programming languages, frameworks, and libraries, and promptly applying any necessary updates or patches. Treating your deployed smart contracts as living entities that require ongoing maintenance and security vigilance is a key aspect of ensuring their long-term security and resilience.
The Principle of Least Privilege: Granting Only Necessary Permissions
When designing and developing your smart contracts, it is vital to adhere to the well-established security principle of least privilege. This principle dictates that contracts, external accounts, and even internal functions within your smart contract should only be granted the absolute minimum necessary permissions required to perform their intended and legitimate functions. For example, if a particular contract only needs to read data from another contract, it should not be granted permission to write data to that contract.
Similarly, a user interacting with your contract should only be granted the permissions necessary to perform their intended action, and no more. By meticulously limiting permissions, you significantly reduce the potential attack surface of your smart contract and minimize the potential damage that could be inflicted in the event that an account or a part of your system is compromised.
Importance of Security Audits: A Critical Examination
The significance of conducting thorough smart contract security audits cannot be overstated. They serve as a vital safeguard, acting as a critical line of defense in identifying and mitigating potential smart contract vulnerabilities before they can be exploited in a live, production environment. Think of a security audit as a rigorous and specialized quality assurance process tailored to address the unique security challenges inherent in decentralized applications and the immutable nature of blockchain technology.
In 2024, audited contracts experienced 98% fewer hacks than unaudited ones, proving the effectiveness of professional audits. The cost of a comprehensive audit ranges from $20,000 to $500,000, but this is a fraction of the potential losses from a single exploit. These statistics highlight the importance of investing in professional audits to ensure the security and reliability of smart contracts.
Unveiling Hidden Weaknesses: The Auditor’s Eye
Professional smart contract security audits involve a meticulous and systematic review of the contract’s source code by highly experienced security professionals. These auditors bring to bear their deep understanding of common smart contract vulnerabilities, known attack patterns, and secure coding best practices.
They carefully analyze the contract’s logic, its overall architecture, and the intricate details of its implementation, diligently searching for potential weaknesses, subtle flaws in the design, and any deviations from established secure coding guidelines. Their specialized expertise allows them to identify complex and nuanced vulnerabilities and potential attack vectors that might be easily overlooked by developers who are primarily focused on the functional aspects of the code.
Learning from Mistakes: The Cost of Neglect
The history of the blockchain space is unfortunately punctuated by numerous high-profile security breaches that serve as stark and costly reminders of the devastating consequences of neglecting to conduct thorough smart contract security audits. A prime example is the attack on the Poly Network in 2021, where a vulnerability in the protocol’s cross-chain communication mechanism allowed an attacker to steal over $600 million in cryptocurrency. As detailed in an analysis by Chainalysis, this massive theft could likely have been prevented with a comprehensive security audit that identified the underlying flaw.
Similarly, the exploit of the Wormhole bridge in 2022, which resulted in the loss of approximately $325 million, further underscores the critical need for rigorous security reviews, even for complex and widely used protocols that have undergone previous scrutiny. According to recent data from Chainalysis, hackers stole a total of $2.2 billion in crypto assets across 303 hacking incidents in 2024, marking a 21% increase from 2023. This trend suggests that even as the market matures, significant cyber intrusions remain a persistent threat.
These incidents clearly demonstrate that investing in professional security audits is not merely an expense; it is a crucial risk mitigation strategy that can save projects from potentially catastrophic financial losses and irreparable reputational damage. As we move into 2025, experts predict that attacks will increasingly target private keys and off-chain vulnerabilities, emphasizing the need for enhanced security measures across all blockchain projects.
The Audit Process: A Step-by-Step Approach
A comprehensive and effective smart contract security audit typically involves a structured and multi-faceted process, encompassing several key stages:
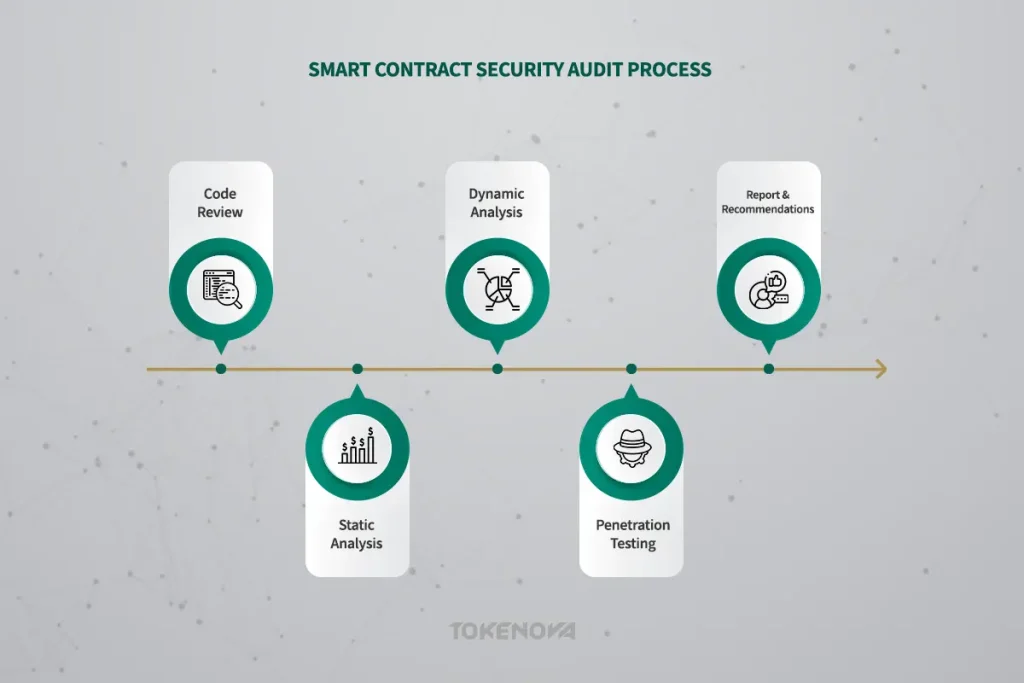
- Code Review: This foundational stage involves auditors meticulously examining the entire source code of the smart contract, line by line, searching for potential vulnerabilities, logical errors in the code’s flow, and any deviations from established secure coding practices and industry standards.
- Static Analysis: In this phase, specialized automated tools are employed to scan the smart contract code for known vulnerability patterns, common coding weaknesses, and potential security flaws. These tools can quickly identify a range of potential issues, providing a valuable initial assessment of the contract’s security posture.
- Dynamic Analysis: To understand how the smart contract behaves in a runtime environment, auditors execute the contract in a controlled test environment using a variety of inputs, both benign and malicious. This dynamic analysis helps to identify potential runtime errors, unexpected behavior, and vulnerabilities that might not be apparent through static analysis alone.
- Penetration Testing: In this more aggressive phase, auditors simulate real-world attack scenarios, attempting to exploit potential vulnerabilities in the smart contract. This “ethical hacking” approach helps to assess the contract’s resilience against various attack vectors and identify weaknesses that could be exploited by malicious actors.
- Report and Recommendations: The culmination of the audit process is the delivery of a detailed report by the auditors. This report outlines all the identified vulnerabilities, provides a clear assessment of their severity and potential impact, and offers specific and actionable recommendations for remediation, guiding the development team on how to address the identified security weaknesses.
Cost-Benefit Analysis of Security Audits
Engaging professional security auditors for a smart contract security audit incurs a direct cost, but it’s essential to consider this expense in the context of risk management and the potential financial impacts of a breach. A cost-benefit analysis shows that the investment is often much lower than the losses from a successful exploit, which could include stolen funds, incident response costs, legal liabilities, and damage to reputation and user trust.
For example, comprehensive audits can range from a few thousand to tens of thousands of dollars, whereas breaches like those affecting Poly Network and Wormhole can lead to losses in the hundreds of millions. Thus, the cost of a security audit can be seen as a prudent investment, preventing significant financial and reputational damage while enhancing investor confidence and long-term project success.
Types of Smart Contract Audits: Choosing the Right Approach
When deciding to undertake a smart contract security audit, it’s important to recognize that there are different approaches available, each with its own strengths, weaknesses, and suitability for various project needs. Selecting the right type of audit is crucial for maximizing its effectiveness and ensuring that it aligns with your project’s specific requirements, budget, and risk tolerance.
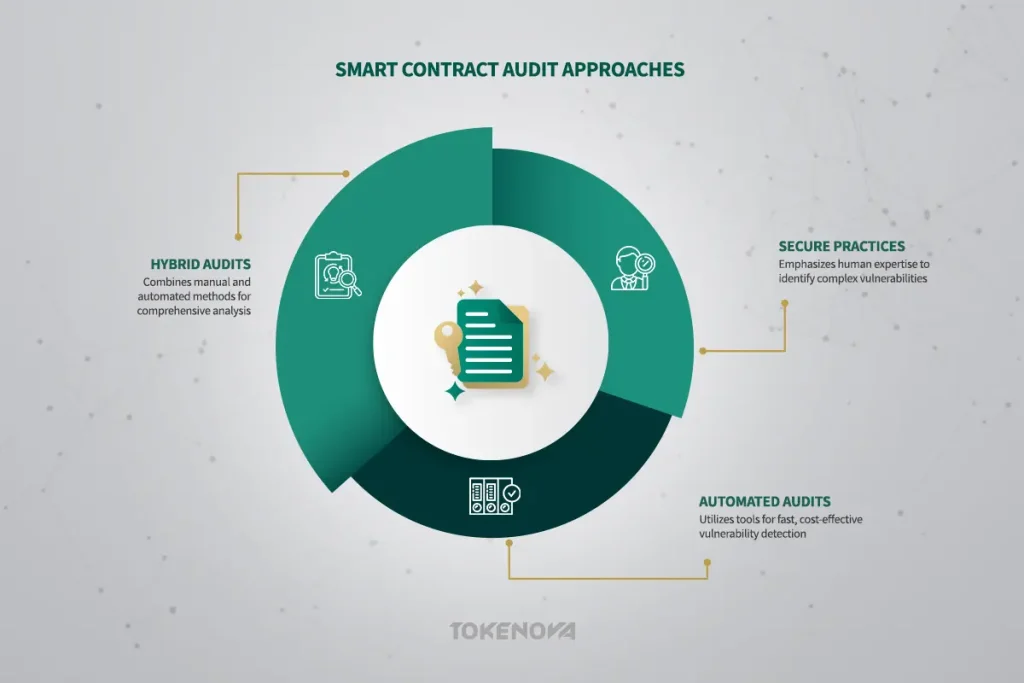
Manual Audits: The Power of Human Expertise
Manual audits place a strong emphasis on the expertise, experience, and critical thinking abilities of human security auditors. In this approach, skilled auditors meticulously review the smart contract code, line by line, leveraging their deep understanding of common smart contract vulnerabilities, known attack vectors, and secure coding best practices.
Manual audits are particularly effective at identifying complex logic flaws, subtle vulnerabilities that might not conform to known patterns, and business logic errors that automated tools might easily miss. The in-depth analysis and nuanced understanding provided by human auditors make manual audits an invaluable investment, especially for critical and highly complex smart contracts where the potential consequences of a security breach are significant.
Automated Audits: Speed and Efficiency
Automated audits primarily rely on the use of specialized smart contract security tools to systematically scan the code for known vulnerabilities, adherence to coding standards, and potential security weaknesses. These audits are generally faster and more cost-effective than manual audits, making them a suitable option for initial security assessments, for projects with more constrained budgets, or for quickly identifying common and easily detectable vulnerabilities. However, it’s important to acknowledge the inherent limitations of automated tools. While they excel at identifying known patterns, they may not be as effective at uncovering novel or complex vulnerabilities that require human intuition and a deeper understanding of the contract’s intended functionality.
Hybrid Audits: Combining Strengths for Thoroughness
Hybrid audits represent a balanced and often highly effective approach, strategically combining the strengths of both manual and automated techniques. In a hybrid audit, automated smart contract security tools are typically used for the initial scan of the code, allowing for the rapid identification of common vulnerabilities and potential areas of concern. This initial automated assessment is then followed by a more in-depth manual review conducted by experienced security experts.
The human auditors focus their attention on the areas flagged by the automated tools, as well as conducting a broader review to identify more subtle or complex vulnerabilities that the automated tools might have missed. This combined approach offers a comprehensive level of security analysis, leveraging the speed and efficiency of automation with the critical thinking and nuanced understanding of human expertise, often providing the most thorough and cost-effective security assessment.
Future Trends in Smart Contract Security: The Evolving Landscape
The domain of smart contract security is a constantly evolving and highly dynamic field, driven by the increasing complexity and sophistication of decentralized applications and the persistent and ever-evolving threat landscape posed by malicious actors. Several exciting and potentially transformative trends are currently shaping the future of how we approach the critical task of securing these essential pieces of code.
In 2025, decentralized audit platforms are fostering community involvement, with ethical hackers earning $100 million for identifying critical issues, a significant increase from previous years. Additionally, cross-chain platforms are undergoing rigorous audits to address interoperability risks, which accounted for 70% of exploit volume. These trends highlight the importance of staying ahead of emerging threats and leveraging community-driven solutions to ensure robust smart contract security.
AI and Machine Learning: The Rise of Intelligent Detection
The integration of Artificial Intelligence (AI) and Machine Learning (ML) technologies holds immense promise for revolutionizing the way we approach automated vulnerability detection in smart contracts. AI and ML algorithms possess the ability to be trained on vast datasets of existing smart contract code, historical vulnerability data, and known attack patterns.
This training enables them to identify subtle patterns, anomalies, and potential security flaws with a level of accuracy and efficiency that surpasses traditional static analysis tools. The application of AI and ML in smart contract security could lead to the development of a new generation of more intelligent, proactive, and adaptive security tools capable of identifying previously unknown vulnerabilities and providing more insightful and actionable security recommendations.
Layer 2 Security: Enhancing Scalability and Protection
The ongoing development and increasing adoption of Layer 2 scaling solutions for blockchain networks are not only addressing the critical challenges of scalability and transaction throughput but also presenting new opportunities for enhancing the security of smart contracts.
Several Layer 2 solutions incorporate built-in security features and innovative mechanisms, such as fraud proofs and validity proofs, which can provide an additional and often robust layer of protection for smart contracts deployed on these platforms. As the adoption of Layer 2 technologies continues to grow, we can anticipate further advancements and innovations in security mechanisms specifically tailored for these environments.
Decentralized Audits: Trust Through Community Review
An emerging and intriguing trend in the smart contract security space is the development and adoption of decentralized audit platforms. These platforms aim to foster greater transparency, community involvement, and distributed responsibility in the smart contract security audit process. Decentralized audit platforms can connect smart contract developers with a wider and more diverse pool of independent security auditors, potentially incentivizing ethical hacking and bug bounty programs through tokenized rewards and reputation systems. By leveraging the collective intelligence and scrutiny of a distributed community of security experts, these platforms have the potential to contribute to a more robust, resilient, and transparent security ecosystem for smart contracts.
Tokenova: Securing Your Decentralized Future
At Tokenova, we deeply understand that robust smart contract security is not merely a technical consideration; it is a fundamental prerequisite for the long-term success, sustainability, and trustworthiness of any blockchain project. Our team of highly experienced and dedicated security consultants provides comprehensive and meticulous smart contract security audit services, employing a strategic combination of cutting-edge automated tools and in-depth manual analysis techniques to identify and effectively mitigate potential smart contract vulnerabilities.
We are committed to working closely with developers throughout the development lifecycle, ensuring that their smart contracts are not only functionally sound but also robust, reliable, and secure, thereby safeguarding their projects, their users, and their valuable assets. Partner with Tokenova to build with unwavering confidence in the transformative power of the decentralized world.

Conclusion
Ultimately, smart contract security is not simply a technical challenge to be overcome; it represents a fundamental requirement for the widespread adoption, continued innovation, and long-term viability of blockchain technology and the burgeoning decentralized ecosystem. By diligently cultivating a deep understanding of common smart contract vulnerabilities, proactively leveraging the ever-evolving landscape of powerful smart contract security tools, and consistently adhering to established and emerging best practices, we can collectively contribute to building a more secure, resilient, and trustworthy decentralized future for all.
As the blockchain industry evolves, adopting AI-driven tools, Layer 2 solutions, and decentralized audits will be crucial for building secure and resilient smart contracts. With advancements in zero-knowledge proofs and cross-chain interoperability, the future of smart contract security looks promising, but vigilance remains key. The adoption of these technologies is paving the way for a more secure and scalable blockchain ecosystem.
Embracing a security-first mindset, prioritizing the investment in thorough and independent smart contract security audits, and empowering development teams with the necessary knowledge, resources, and a culture of security awareness are all essential steps in ensuring the continued growth and success of the decentralized web. The future of decentralized applications and the trust placed in them depend on our collective commitment to making security a paramount concern.
Key Takeaways
- Robust smart contract security is absolutely essential for protecting decentralized applications from potentially devastating exploits and significant financial losses.
- A thorough understanding of common smart contract vulnerabilities, such as reentrancy attacks, integer overflows, and denial of service vulnerabilities, is crucial for developers.
- Leveraging a range of sophisticated smart contract security tools, including static analyzers and formal verification tools, is vital for identifying potential weaknesses in code.
- Conducting comprehensive smart contract security audits performed by experienced and independent security professionals before deployment is a non-negotiable step in ensuring the security of your applications.
- Implementing security best practices throughout the entire smart contract development lifecycle, including the use of safe math libraries and the implementation of robust access control mechanisms, is paramount for building secure and resilient applications.